Driving Security Innovation in The Cloud Native Community
Our goal is to ensure that security drives faster adoption of cloud native technologies and processes, while avoiding security risks. Open source drives this forward.
Accelerate Adoption
On-Ramp to Security
Dedicated to Open Source
Accelerating Cloud Native Adoption
Security is often cited as the #1 concern to hinder cloud native adoption. Open source allows us to educate engineering, security, and DevOps teams through accessible tools, reducing the skills gap and automating security controls into cloud native pipelines well before applications go into production.
The Open Source
On-Ramp to Security
On-Ramp to Security
Our open source tools help users get hands-on, effective security tooling that can immediately address their most burning concerns. Our open source users may graduate to our commercial tools when reaching a certain scale or level of complexity, but our open source tools are designed to be used independently and provide value “as is”.
Open Source Is Not Just Our Hobby
At Aqua we’ve built a team exclusively dedicated to open source, separate from our commercial engineering team. This ensures we can commit, long term, to creating and maintaining high quality code, and ensure ongoing involvement in contributing to other open source community projects.
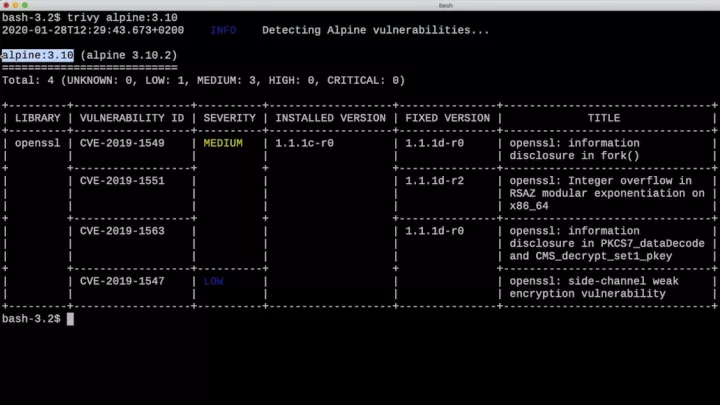
 trivy
trivy
Manage vulnerabilities in your pipeline
The most comprehensive and easy-to-use open source vulnerability scanner for container images
- Detects vulnerabilities in OS packages and application dependencies
- Fast, stateless scanning with no prerequisites for installation
- Easy integration into CI tools
- Highly accurate and comprehensive results
Go

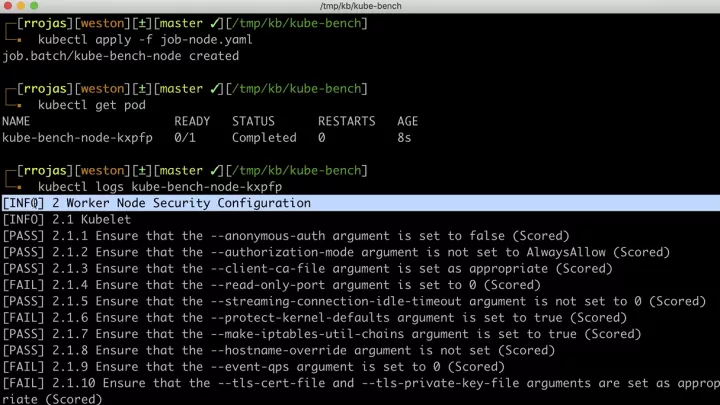
 kube-bench
kube-bench
Securely configure your Kubernetes clusters
The industry standard tool for checking Kubernetes compliance with the Center for Internet Security (CIS) Benchmark
- Auto-detect correct tests per node type and version
- Customizable test definitions through YAML
- Special definitions for Red Hat’s OpenShift hardening guide
Go


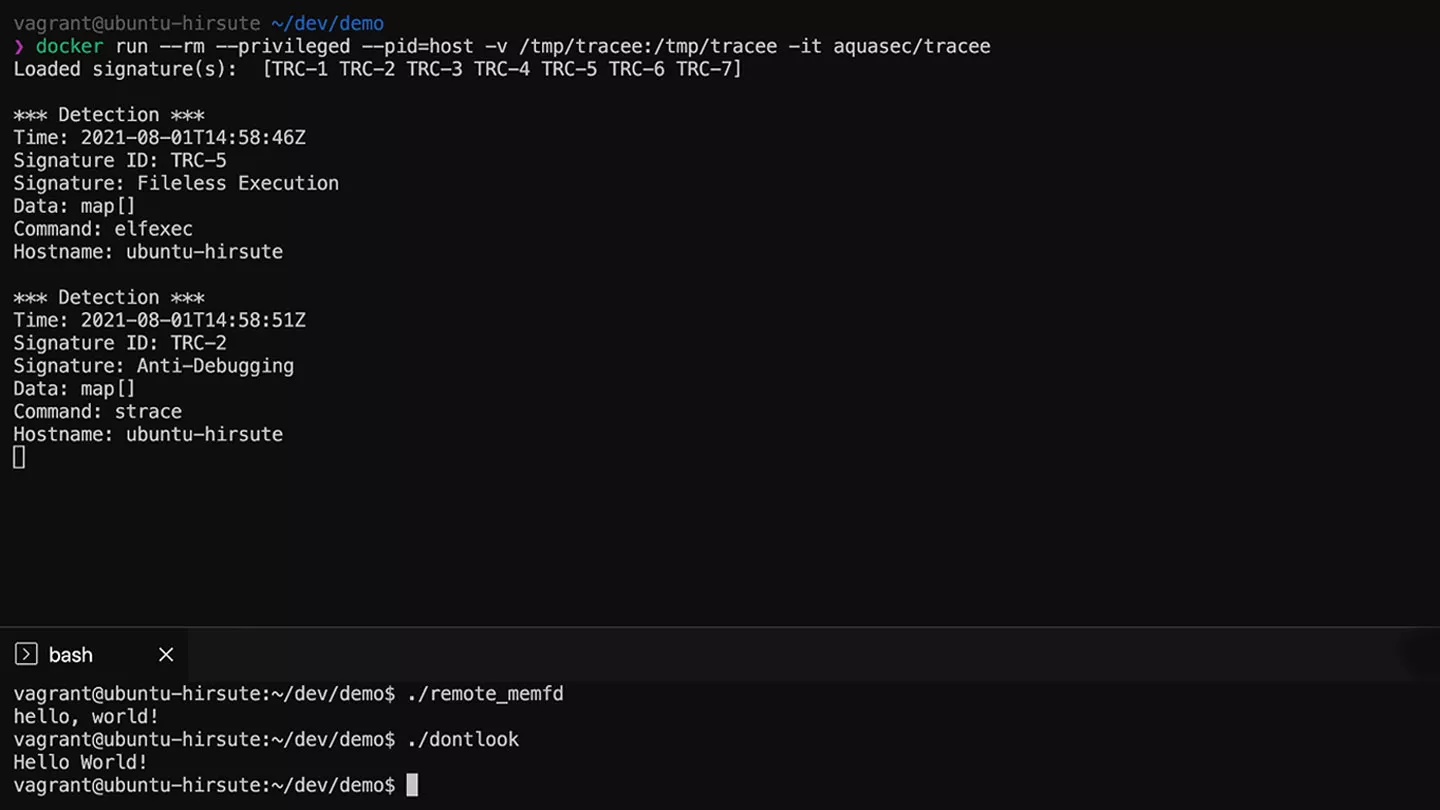
 tracee
tracee
Linux Runtime Security and Forensics using eBPF
Detect suspicious behaviors at runtime using eBPF tracing and research-driven behavioral signatures.
- Security grade accurate system tracing thanks to eBPF based kernel probes
- Turn-key runtime security thanks to an included library of behavioral signatures by Aqua Security’s Team Nautilus
- Flexible rule engine, customizable using Open Policy Agent policies
eBPF


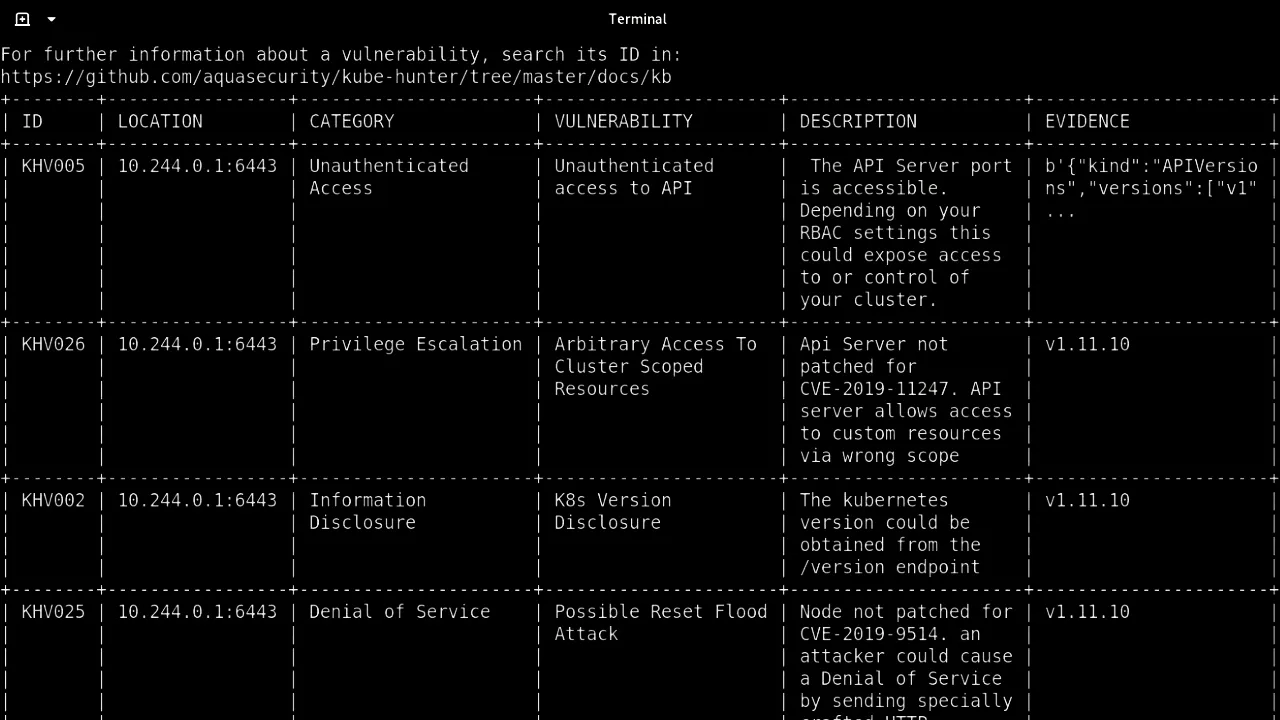
 kube-hunter
kube-hunter
Test your Kubernetes setup against exploits
Penetration testing that simulates dozens of attack vectors on your Kubernetes cluster
- Run either as external unauthorized user, or in a pod to simulate the consequences of a compromised container
- Active mode shows proof of pen-test success
Visibility into real-world exposure to risk
Python

Additional Open Source Tools and Contributions
CloudSploit
Ensure cloud compliance and secure configuration with Cloud Security Posture Management
kubectl-who-can
See who has permission to perform specific actions on K8s objects
