Secure Your Modern Applications With Complete Lifecycle Container Security
Ensure complete end-to-end protection of containers across all platforms and clouds from build through runtime with the industry-leading container security solution.
Learn MoreAccurately Detect Risks in Container Images
Reduce the container attack surface by continuously scanning images to uncover known vulnerabilities, hidden malware, embedded secrets, misconfigurations, open source issues, and more with a premium version of the award-winning cloud native security scanner Aqua Trivy.
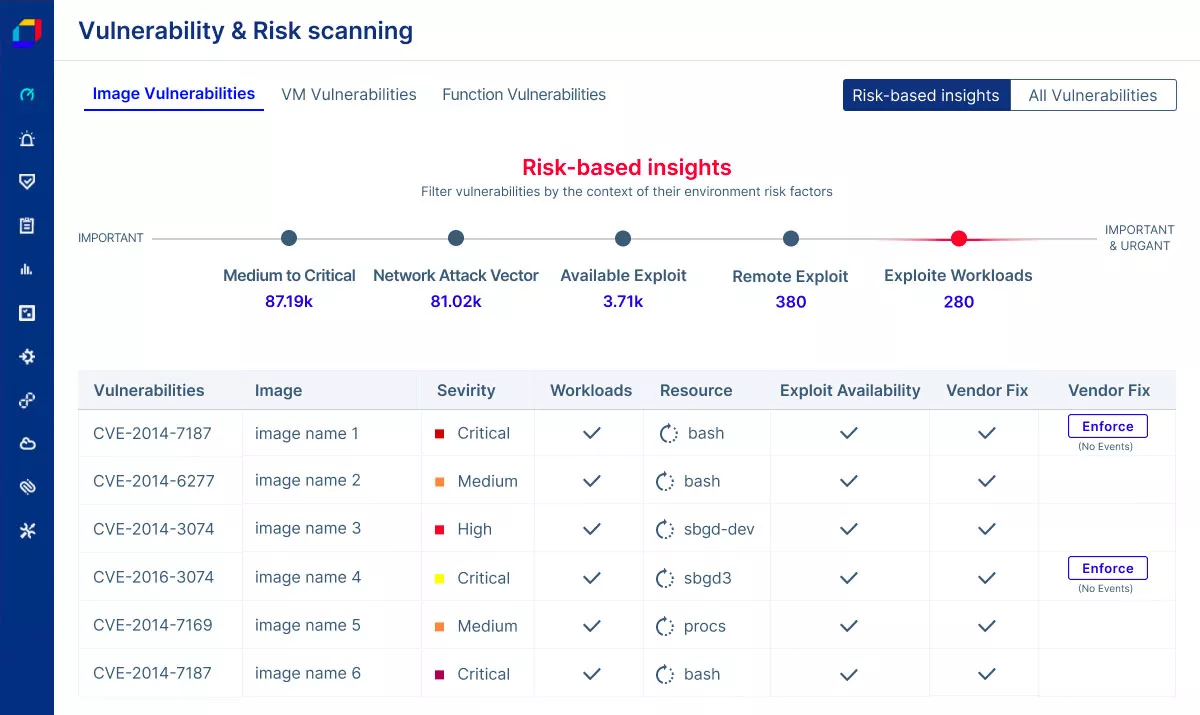
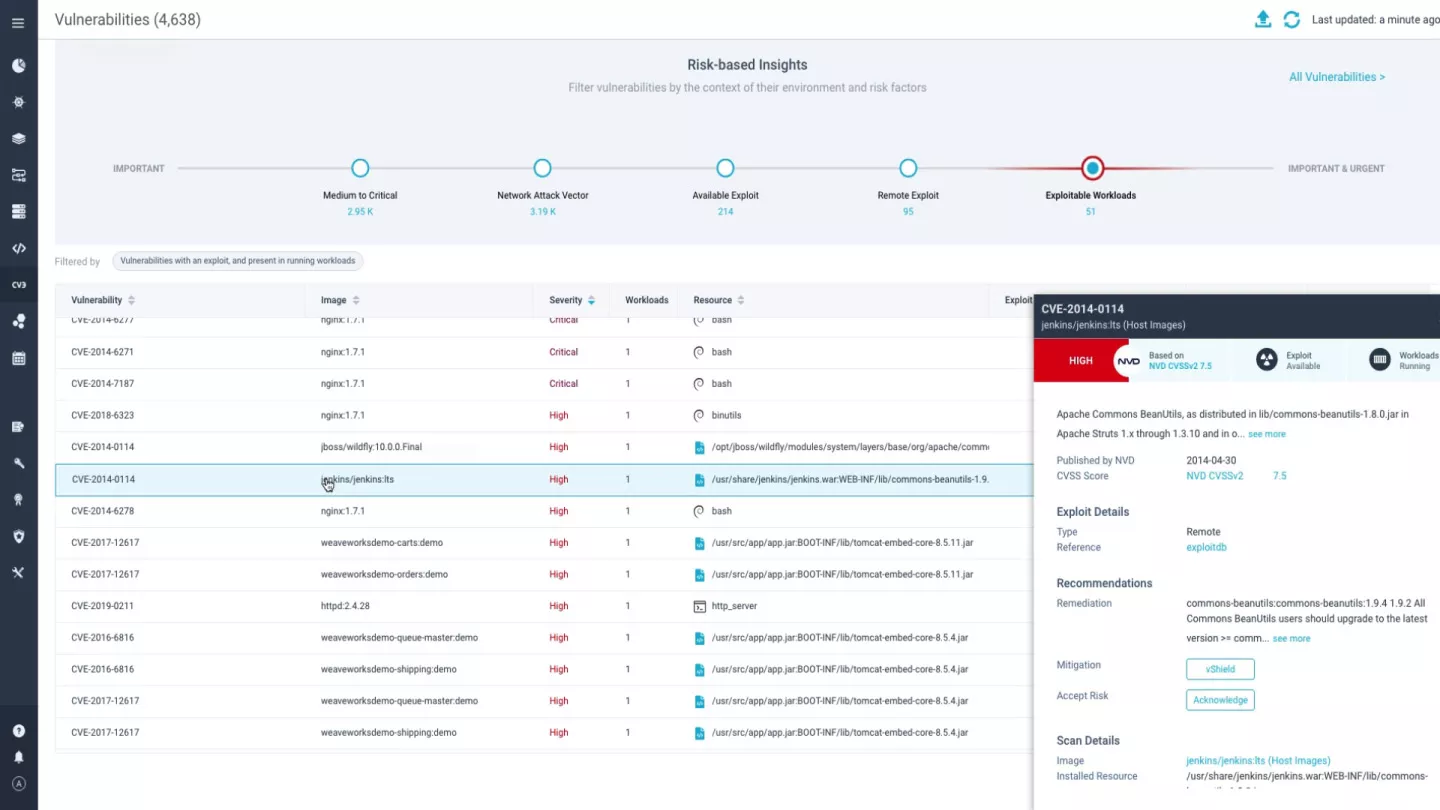
Reduce Vulnerability Detection Time
Automatically generate a prioritized list of vulnerabilities using a wide range of risk-based contextual factors such as exploitability, risk score, severity, and whether the workloads are running, helping to clearly prioritize vulnerabilities for remediation.
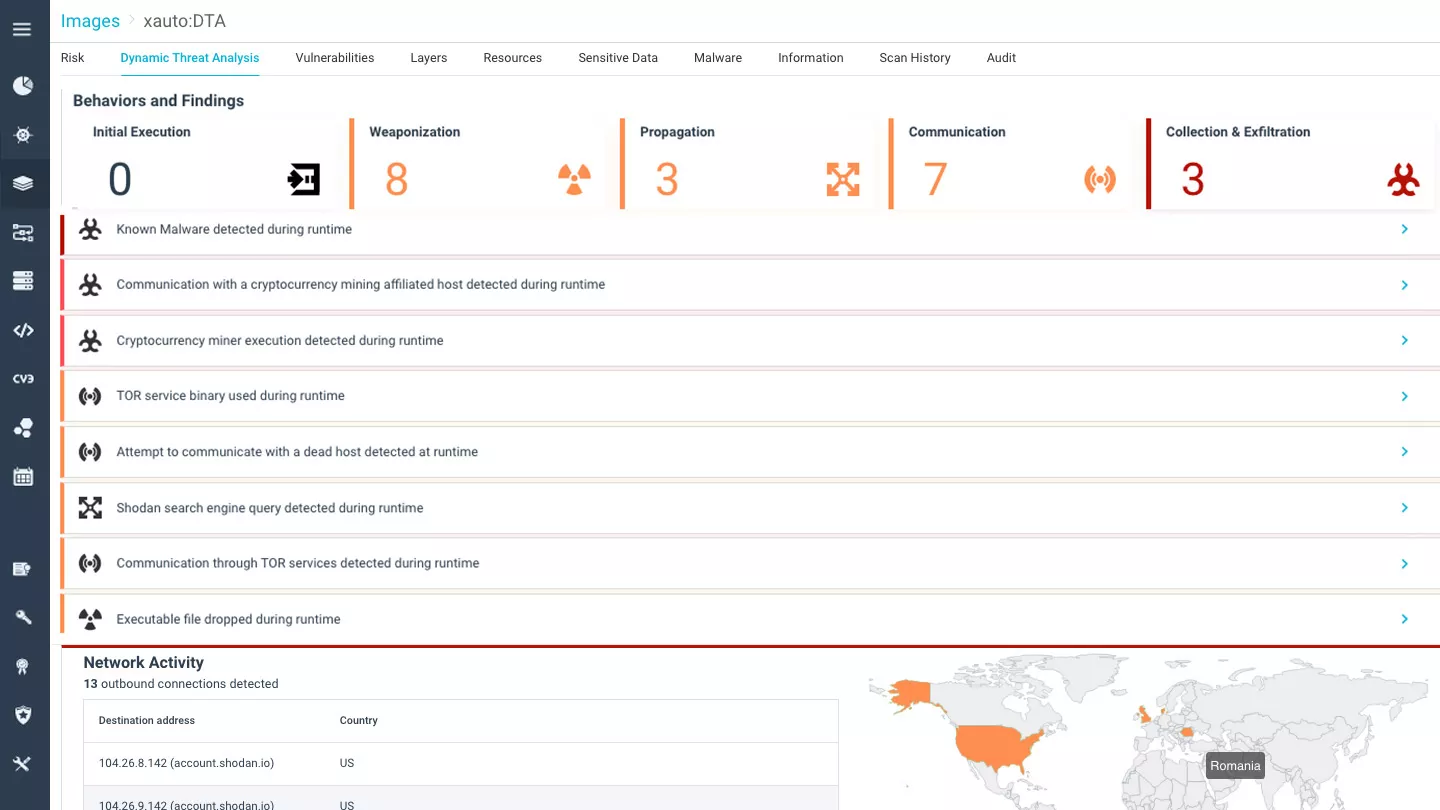
Prevent Malicious Threats from Reaching Production
Uncover malicious threats in container images before they are pushed to deployment, effectively preventing them from causing any damage to your production environment. Run container images in a secure virtual sandbox to detect sophisticated threats that often evade static scanning such as fileless malware, advanced supply chain and zero-day attacks.
Deploy Only Trusted Images
Establish acceptance gates for your runtime environment by setting up flexible assurance policies that prevent unapproved container images from advancing to deployment, defining clear risk levels while reducing operational errors, image sprawl, and rogue deployments. Tailor policies and rules based on the security needs of different applications or pipelines.
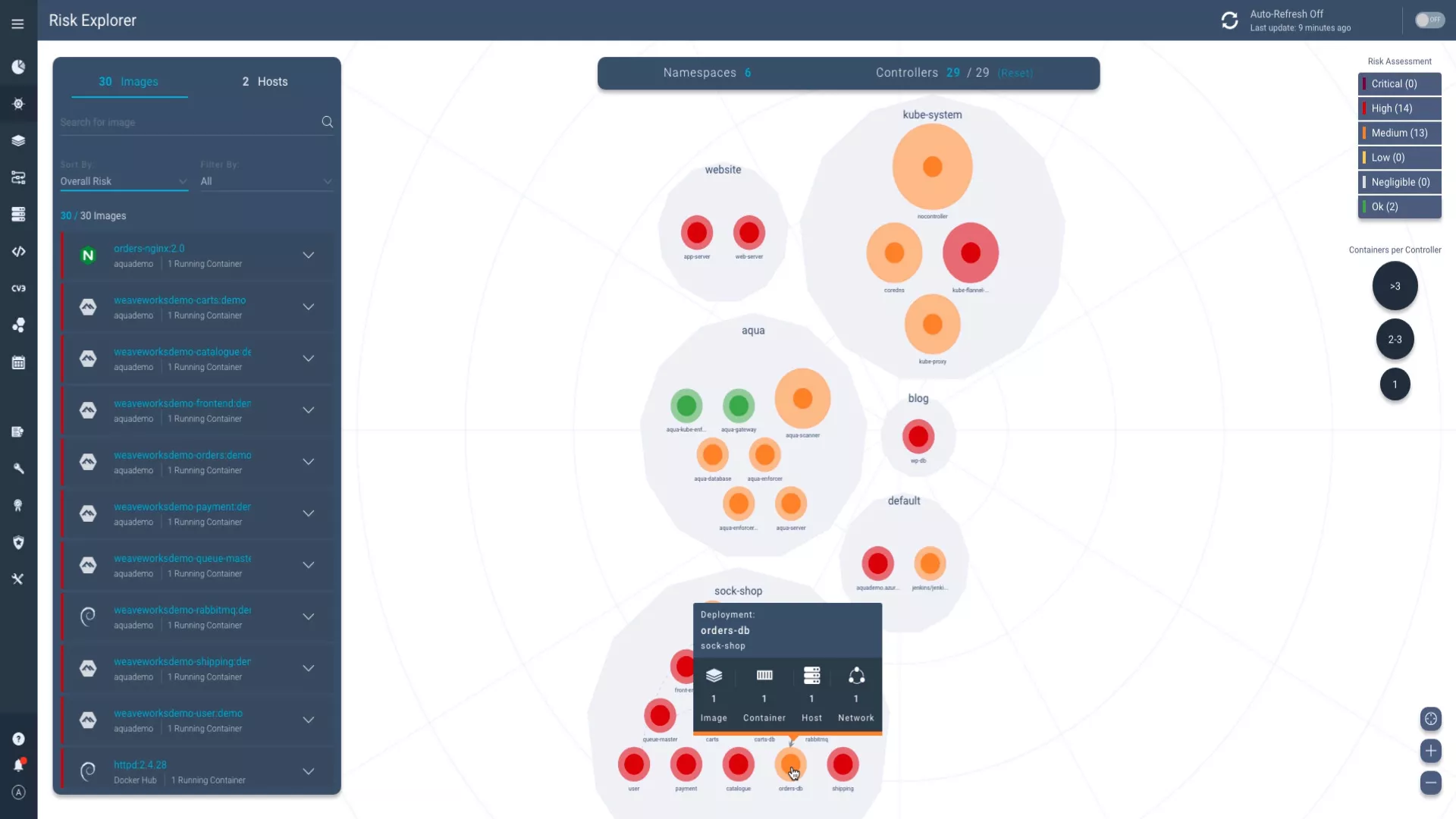
Secure Containers at Runtime
Safeguard container workloads in production against a wide range of threats with robust runtime security, powered by real-world threat intelligence. Gain complete workload visibility and enforce granular controls across hybrid and multi-cloud environments. Save time with preconfigured runtime policies and simple deployment, eliminating the need for specialized security expertise
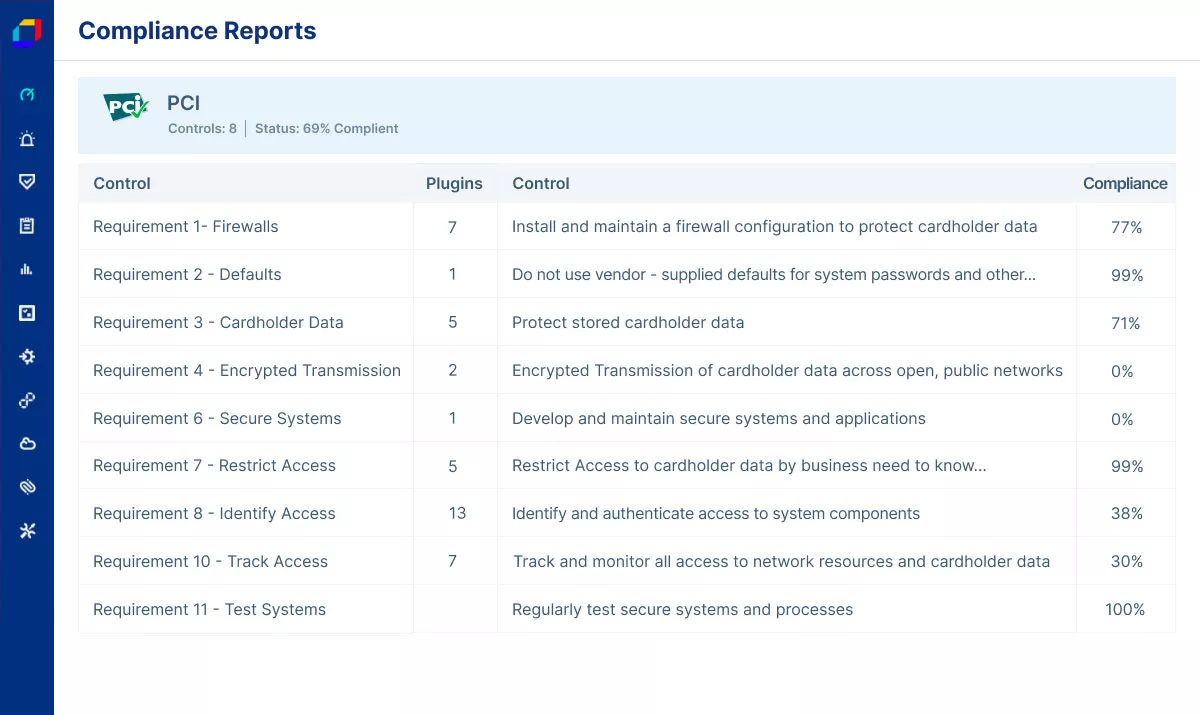
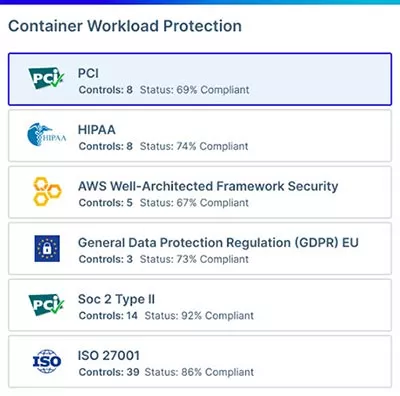
Report Compliance with Ease
Achieve, manage, and demonstrate compliance of your container-based applications by automatically auditing your security posture for drifts and violations across dozens of common industry frameworks and standards such as NIST, PCI DSS, GDPR, and CIS Benchmarks.