In the past couple of days there has been many troubling publications and discussions about a mysterious critical Linux vulnerability allowing remote code execution. While this headline is very alarming, after diving into details there are many preconditions that cool down the level of alertness. Aqua Security researchers have looked into the content that was released and prepared this blog to answer frequently asked questions regarding a series of vulnerabilities in the Common UNIX Printing System (CUPS).
What is CUPS?
Common UNIX Printing System (CUPS) is an open source printing system that allows a computer to act as a print server. It manages print jobs and queues and provides support for printing via the Internet Printing Protocol (IPP), making it a widely used printing service on UNIX-like operating systems, including Linux and macOS.
What are the vulnerabilities that were published?
On September 26 Simone Margaritelli, a security researcher, published a blog post that sums up the vulnerabilities.
According to Margaritelli, a remote unauthenticated attacker can exploit vulnerabilities in printer systems to replace or install new IPP (Internet Printing Protocol) URLs. This allows the attacker to execute arbitrary commands on the target computer when a print job is initiated, without the user’s knowledge. Having said that, Margaritelli noted that there are some conditions for this vulnerability to be exploited.
These are the conditions:
- The cups-browsed service has manually been enabled or started.
- An attacker has access to a vulnerable server, which allows unrestricted access, such as the public internet, or Gains access to an internal network where local connections are truste.
- Attacker advertises a malicious IPP server, thereby provisioning a malicious printer.
- A potential victim attempts to print from the malicious device.
- Attacker executes arbitrary code on victim’s machine.
The published CVEs are:
- CVE-2024-47176
cups-browsed <= 2.0.1 binds on UDP INADDR_ANY:631trusting any packet from any source to trigger aGet-Printer-AttributesIPP request to an attacker controlled URL. - CVE-2024-47076
libcupsfilters <= 2.1b1 cfGetPrinterAttributes5does not validate or sanitize the IPP attributes returned from an IPP server, providing attacker controlled data to the rest of the CUPS system. - CVE-2024-47175
libppd <= 2.1b1 ppdCreatePPDFromIPP2does not validate or sanitize the IPP attributes when writing them to a temporary PPD file, allowing the injection of attacker controlled data in the resulting PPD. - CVE-2024-47177
cups-filters <= 2.0.1 foomatic-ripallows arbitrary command execution via theFoomaticRIPCommandLinePPD parameter.
A proof-of-concept (PoC) developed by Margaritelli is included in the GitHub advisory for CVE-2024-47176. Additionally, a PoC has been published on GitHub based on a commit in the OpenPrinting CUPS repository.
Detecting if my host is vulnerable
You can use the following command to determine if cups-browsed is running:
$ sudo systemctl status cups-browsed
If the result includes Active: inactive (dead) then the exploit chain is halted and the system is not vulnerable.
If the result is running or enabled, and the BrowseRemoteProtocols directive contains the value cups in the configuration file /etc/cups/cups-browsed.conf, then the system is vulnerable.
You can also check if port 631 is exposed listening to upd
netstat -tuln | grep 631 or ss -tuln | grep 631
If so, you can delete it from the configuration file at /etc/cups/cupsd.conf.
Mitigation
Advised to disable and remove cups-browsed from vulnerable systems. Additionally, CUPS is set to listen on UDP port 631, so it is advised to block all traffic to UDP port 631.
Mitigation of these vulnerabilities is as simple as running two commands, especially in any environment where printing is not needed.
To stop a running cups-browsed service, an administrator should use the following command:
$ sudo systemctl stop cups-browsed
The cups-browsed service can also be prevented from starting on reboot with:
$ sudo systemctl disable cups-browsed
Once a patch is available, use it or upgrade to a non-vulnerable cups version.
How Aqua Can Help?
Aqua Enforcer can block the cups-browsed service from running. It can also be used to identify which hosts have the cups-browsed packages and mark these hosts as non-compliant.
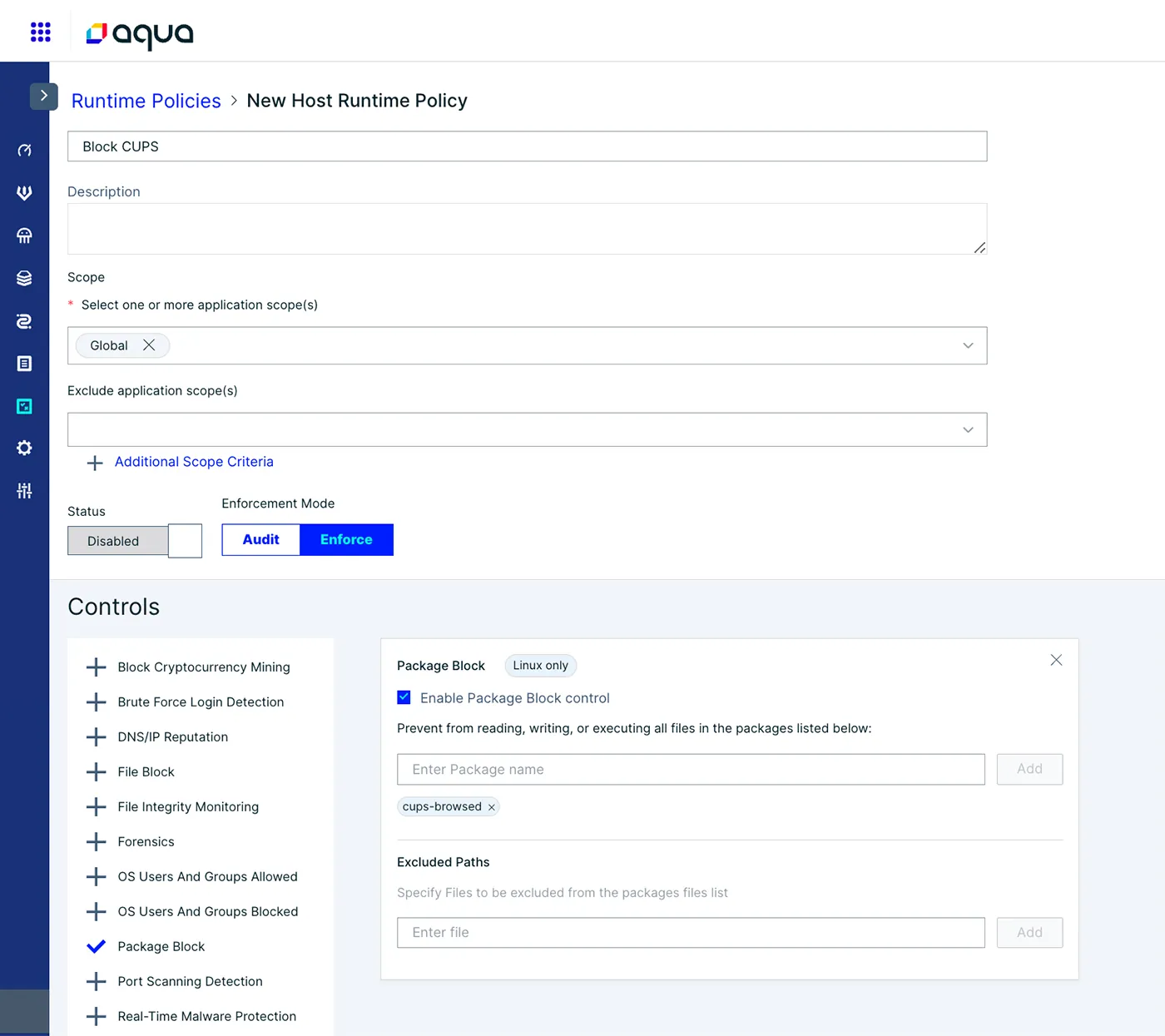
Runtime Policy
Create a Runtime Policy to blocks the cups-browsed package from running. This policy should be put in Enforce mode.
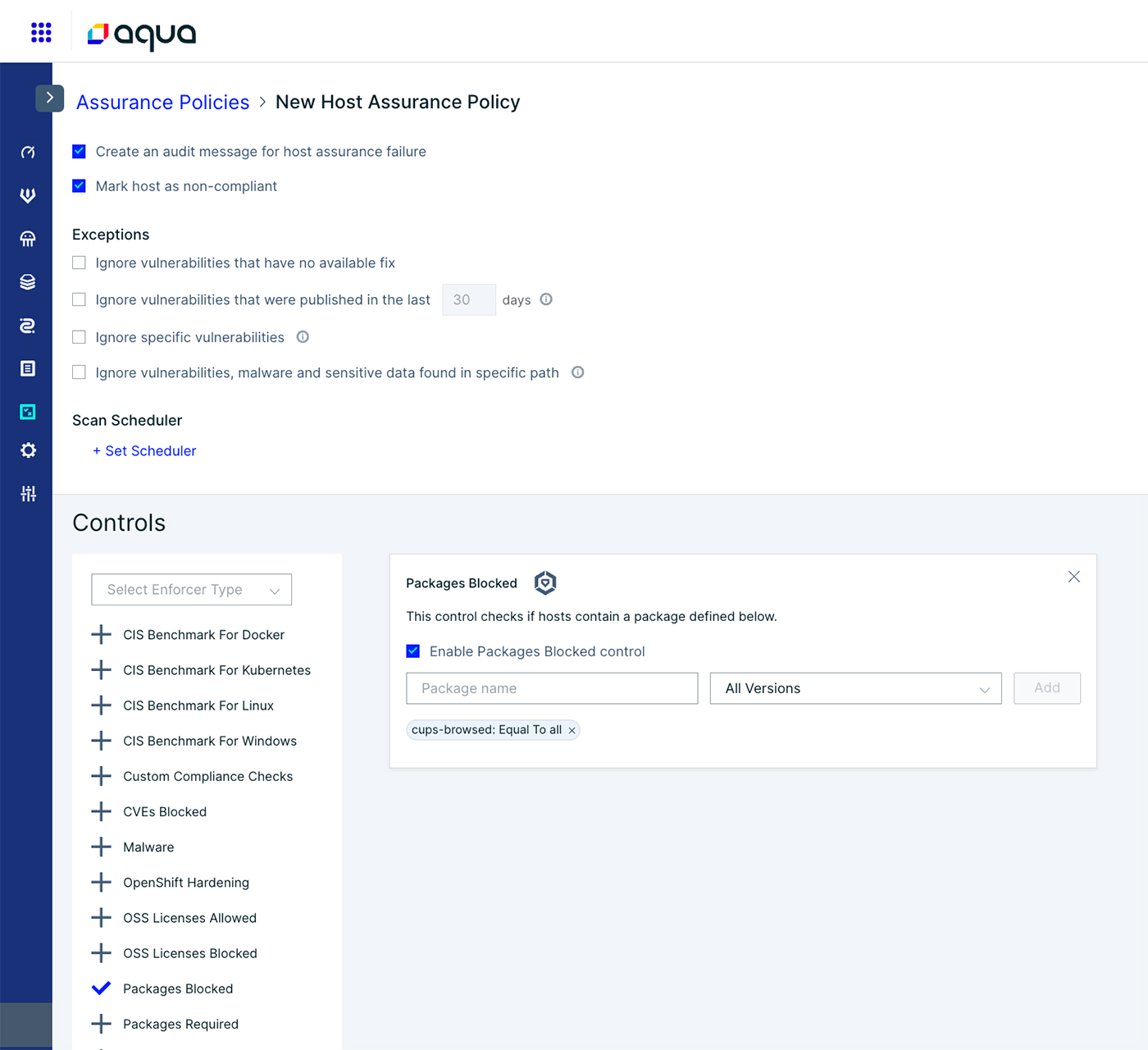
Host Assurance Policy
Create a host assurance policy to identify hosts that have the cups-browsed service.
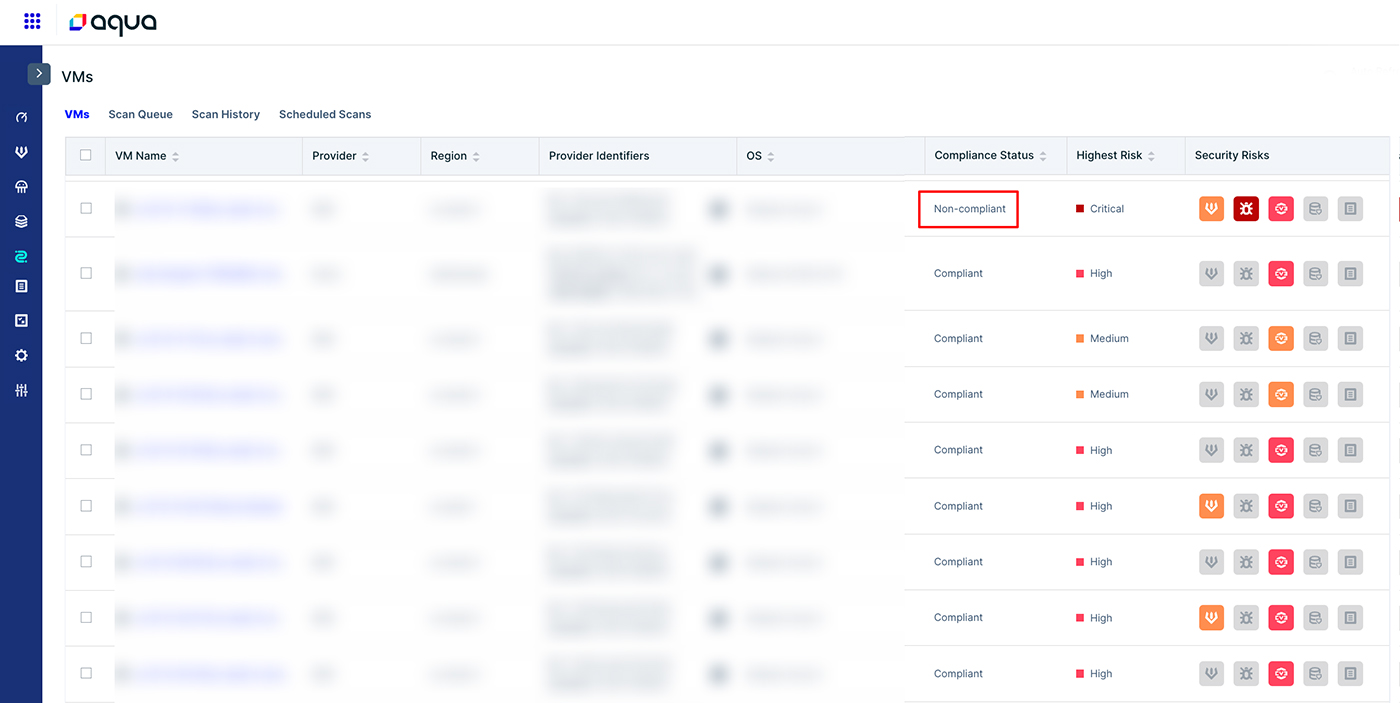
You can find all the non-compliant VMs that have the cpus-browsed package, which will be shown as non-compliant.