For many years, threat actors have been using legitimate remote access tools (RATs) in their campaigns, tricking users into installing them to get full control over the victims’ systems. Similarly, in the cloud native world, attackers are increasingly targeting user interface (UI) tools to gain access to Docker and Kubernetes instances. In this blog, we’ll explain how misconfigured UI tools can allow access and control over cloud native environments and describe the techniques that threat actors use to exploit UI tools for their benefit.
A year ago, we first learned that attackers are using UI tools to get access to Docker and Kubernetes environments. Since then, this phenomenon has expanded, and today malicious actors are using various techniques to exploit UI tools.
Kubernetes UI tools
Many applications can be considered Kubernetes UI tools. Some of them, such as cAdvisor and Kubernetes Operational View, only provide visibility into the cluster. Others also enable access and control. In this analysis, we looked at the latter, since these tools can cause far more damage when exploited by an attacker. We focused on the following tools:
- Weave Scope: a visualization and monitoring tool for Docker and Kubernetes. It enables real-time access to applications and infrastructure, allowing you to view logs and diagnose problems. Weave Scope can also be used to manage Docker containers, which includes operations such as starting, pausing, stopping, and restarting containers as well as launching a command line.
- Kubernetes Dashboard an official web-based UI designed for Kubernetes The dashboard can display all workloads that are running in the cluster. It also includes features to control and modify workloads and display pod activity logs. In addition, you can view basic resource usage on Kubernetes nodes.
- Octant an open source web interface for inspecting a Kubernetes cluster and its applications. Octant allows visibility into clusters, as well as debugging, streaming container logs, and interaction via a command line interface.
What can threat actors do with UI tools?
We set out to examine the state of misconfigurations in these three UI tools. We assume that some of these dashboards are honeypots set by security researchers like us. However, some of the exposed UIs have signs of real environments, and a few of them were even actively exploited by attackers.
Weave Scope
To find the Weave Scope dashboards, we queried Shodan, a search engine for Internet-connected devices, and got 58 results. After removing irrelevant results and password-protected dashboards, we found 10 dashboards that were exposed to the Internet.
These dashboards allow an attacker full visibility into your Kubernetes environment. In addition, the UI displays inbound and outbound traffic, making it easy to detect malicious communication, for example, the communication of the Tsunami malware with its server over IRC protocol.

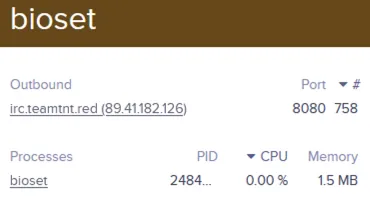
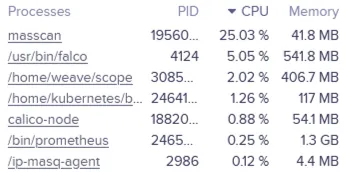
Weave Scope also provides visibility into the process behind this communication. This aligns with the TeamTNT’s modus operandi. Below, you can see that the attackers are running masscan along with other applications that run on the host. Weave Scope can see what the underlying host may miss since the threat actor is using a rootkit to hide high CPU usage and massive scanning activities.
Kubernetes Dashboard
We queried Shodan to find the Kubernetes Dashboards and got 2,073 results. After cleaning up those results, we ended up with 27 dashboards that don’t require user authentication, which leaves the environment exposed to exploitation.
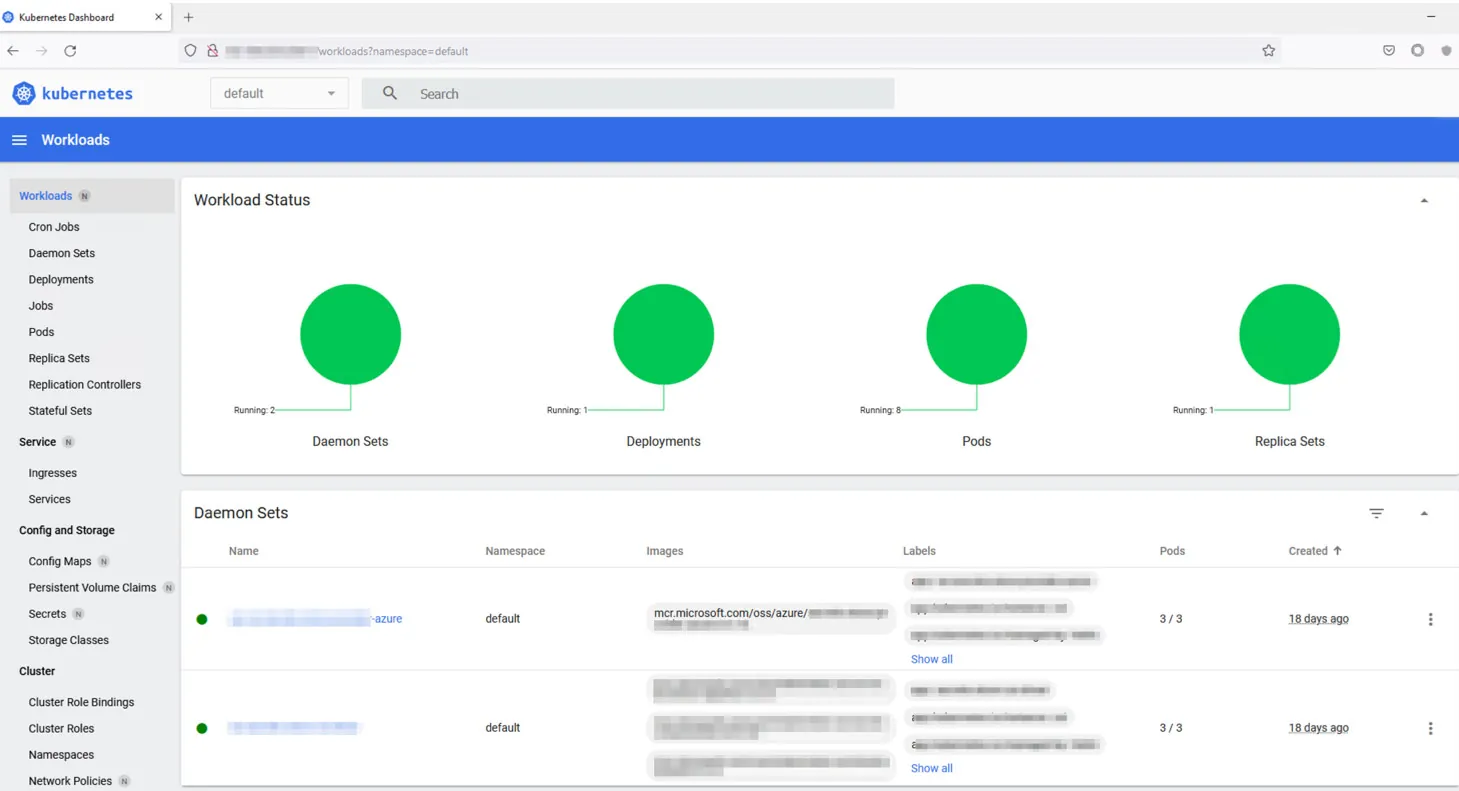
As you can see in the screenshot below, the exposed Kubernetes Dashboard allows an attacker full visibility into your Kubernetes environment:
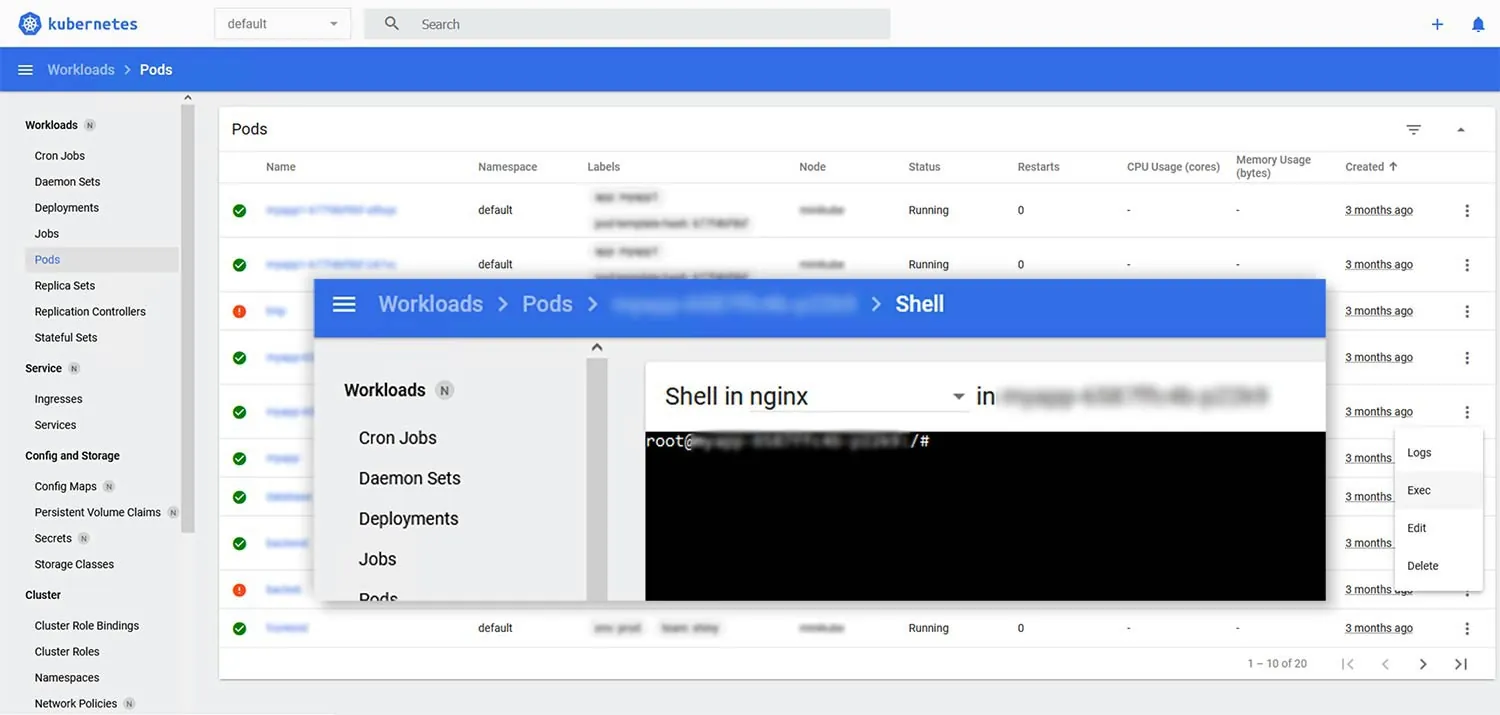
Attackers can open a shell connection to a running pod and can start containers and change deployments.
The Kubernetes Dashboard also contains secrets that can easily be accessed.
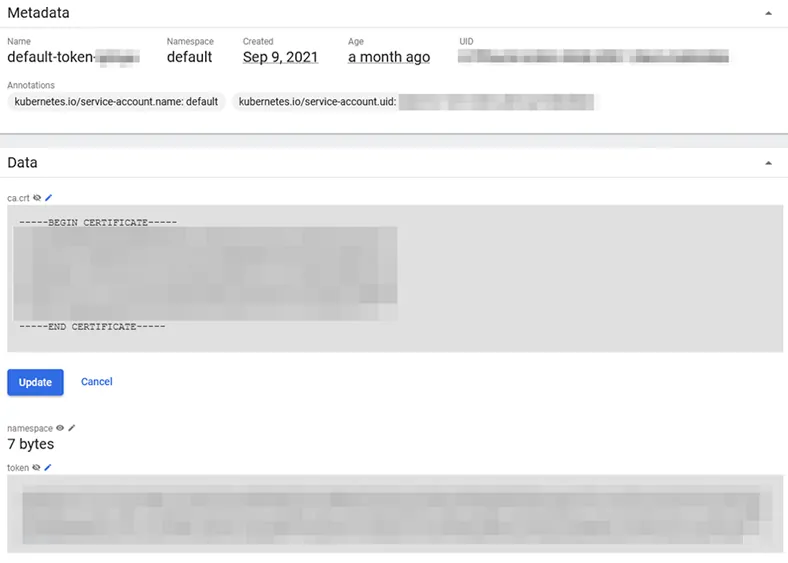
On top of this, there are many other ways for an attacker to cause damage, such as changing settings and getting volumes.
This attack vector is not new. In the past, companies such as Tesla were attacked via a misconfigured Kubernetes Dashboard.
Octant
We did the same to find the Octant dashboards and got nine results. After getting rid of irrelevant results and password-protected dashboards, we were left with four dashboards that don’t require user authentication and that, therefore, leave the environment exposed to exploitation. However, they all seem to be honeypots.
That said, below are some examples of what an attacker could do with an exposed Octant dashboard.
As you can see in the screenshot, the Octant dashboard allows an attacker full visibility into your Kubernetes environment.
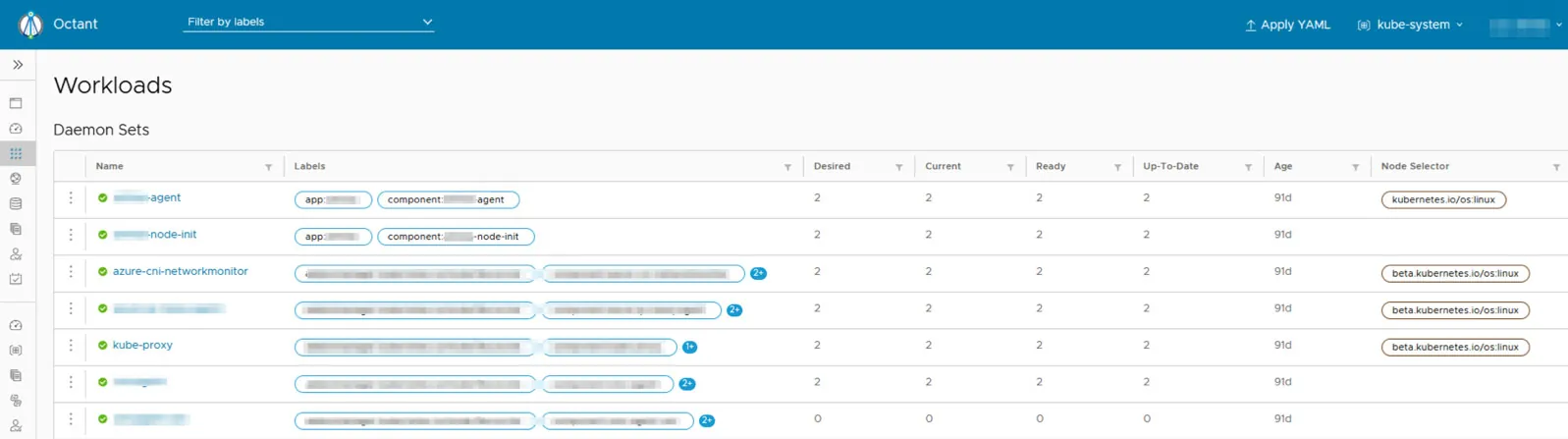
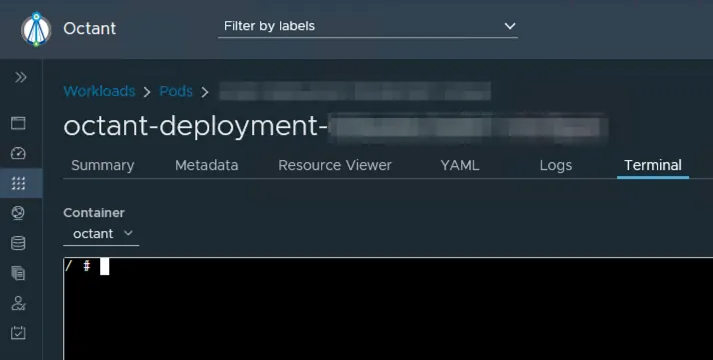
Attackers can open a shell connection to a running pod and can start containers and change deployments.
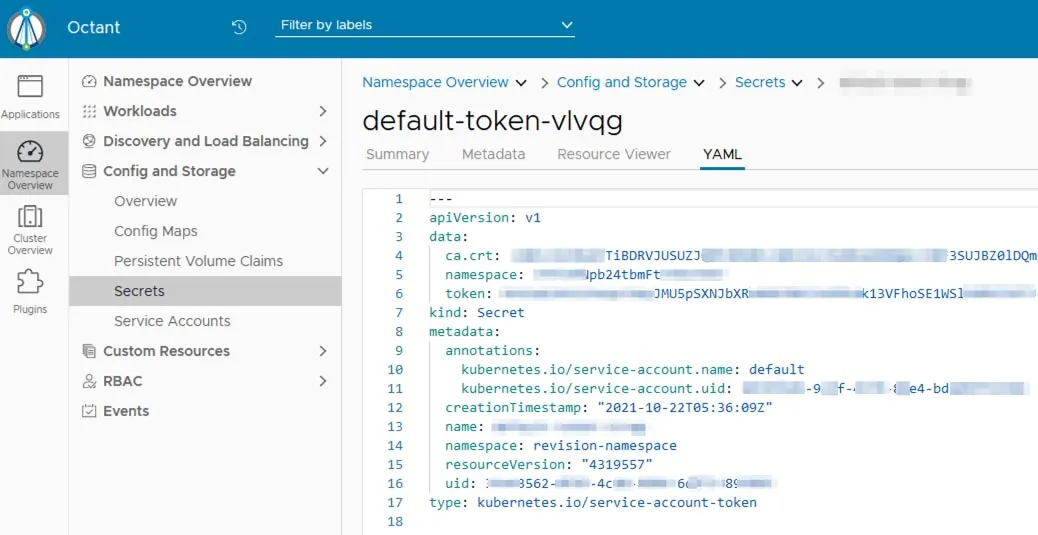
Octant also contains secrets that can easily be accessed.
To dive deeper, there’s a great blog by Jack Wink that demonstrates how to take over a cluster through Octant.
To our knowledge, when used as part of the managed Kubernetes services, these UI tools are set with no misconfigurations. Therefore, we conclude that these misconfigured instances were created manually due to human error or lack of knowledge.
Mitigation recommendations
Hardening and correct configuration of cloud services can significantly reduce the potential attack surface and prevent attacks that target misconfigured Kubernetes UI tools. To protect yourself from threats like this, it’s important to follow Kubernetes security best practices.
Over the past few months, Aqua’s experts have written several guides on Kubernetes security and hardening, including:
- Top 10 Kubernetes Application Security Hardening Techniques
- Protecting Kubernetes Secrets: A Practical Guide
We strongly advise creating an allow list to images that were tested and vetted and were found as compliant and clean of malware and vulnerabilities. With Aqua, you can set that only these containers will be allowed to run.
If you’re not using Kubernetes UI tools, we recommend limiting the activation of these tools during runtime. This can be done by using Aqua’s runtime policies to block these containers.
At runtime, Aqua’s drift prevention can block the execution of a binary that is designed to launch Scope, Kubernetes Dashboard, or Octant.
Also, Aqua maintains a list of blocked domains and IP addresses (such as teamtnt[.]red). The communication with these domains or IP addresses can be blocked to prevent malicious payload dropping.
Additionally, Aqua’s advanced malware protection can prevent download and execution of known threats.
Summary
The Kubernetes UI dashboards are useful tools aimed at giving developers visibility into their clusters. However, a misconfigured UI tool can leave your organization exposed to serious attacks, giving the attackers full control over your environment. The variety of techniques that threat actors are using underscores just how popular this attack vector has become.

