VEX (Vulnerability eXploitability Exchange) is an emerging industry standard for communicating the relevance and impact of security vulnerabilities on software artifacts. This approach allows software maintainers to indicate when a specific vulnerability in a software dependency is irrelevant to their software due to the specific use case of that dependency. By conveying this crucial information to scanning tools via VEX, the accuracy of scan results is improved, leading to more actionable vulnerability reports for end users.
VEX encompasses several implementations, including OpenVEX, CSAF VEX, and CycloneDX VEX. The core elements of a VEX document are:
- The vulnerability being discussed, typically identified by a CVE ID
- The product in question, usually identified by a software package ID
- The status of that vulnerability within the software.
Today, the Trivy team is excited to announce VEX Hub, a centralized, comprehensive, and vendor-neutral repository for VEX statements. VEX Hub offers a unified repository that enhances the quality and clarity of security reports, standing out in the vulnerability scanning landscape. In this blog post, we’ll explore how VEX is currently used and how VEX Hub can help you obtain better security insights.
VEX in Trivy
As the leading open source vulnerability scanner, Trivy has promoted and supported VEX since its early days. With the --vex flag users can pass a VEX document for Trivy to consider. If Trivy finds a vulnerability in an artifact that is addressed by the provided VEX document, it will be suppressed by Trivy.
This feature makes it possible for users to consume VEX documents, but there’s still an implicit assumption that the user knows where and how to obtain these documents. Even if they do, users still need to manage an entire workflow around discovering, fetching, and feeding VEX documents to the scanning tool. As we observed the VEX ecosystem evolve, we hoped for a solution to emerge. Realizing that no one was better positioned to take the initiative and lead the way, we created VEX Hub.
VEX Hub
VEX Hub is the missing repository of VEX statements. It aggregates VEX documents from software maintainers and organizes them in a central repository that is accessible for integration. With VEX Hub, software maintainers can easily make VEX documents widely available to their users, and scanning tools can easily lookup relevant vulnerability information. Most importantly, with VEX Hub, users get more accurate and actionable vulnerability reports.
How does it work?
- Software maintainers create VEX statements for their software and store it in the same source code repository of their software code.
- VEX Hub crawls source code repositories and collects VEX documents in an organized VEX Repository.
- Trivy connects with VEX Hub to discover, fetch, and consume VEX statements from VEX Hub. It’s all fully automated.
Committed to openness
VEX has the potential to become pivotal to the security industry, and this is why we want to make VEX Hub accessible to everyone. We have designed VEX Hub in an open, interoperable, and vendor-neutral way. All the content is openly hosted as files on GitHub, the API is a simple HTTP endpoint, and everything is thoroughly and formally documented in the open VEX Repository specification. Trivy is the first security scanner to leverage VEX Hub, but others are welcome to join!
How to participate?
- If you are a package maintainer, add VEX statements for your software and make it available in VEX Hub. Follow this guide to learn more:
- If you are software distributor, publish VEX statements in a VEX Repository format so that Trivy and other scanners can leverage it in addition to VEX Hub.
- If you are building a vulnerability scanner, start consuming VEX repositories to deliver the value of VEX to your users.
- If you are an end user of vulnerability scanner, ask your vendors to support VEX and VEX Repositories.
The design and implementation of VEX Hub, VEX Repository, VEX Crawler, and Trivy’s VEX support are all open source. We welcome and encourage collaboration across this stack.
VEX Hub in Trivy
VEX Hub was released with Trivy v0.54 (released in July 2024). If you are running this version of later, you can use VEX Hub in your Trivy scans. VEX Hub support is currently optional and can be enabled using the --vex repo flag.
That’s it! During the scan, Trivy will:
- Discover registered VEX Repositories, which by default include just VEX Hub.
- Connect with VEX Hub and ensure the latest copy is available locally.
- Perform a vulnerability scan and apply relevant VEX suppressions automatically.
This should result in fewer false-positives and more accurate and actionable vulnerability reports.
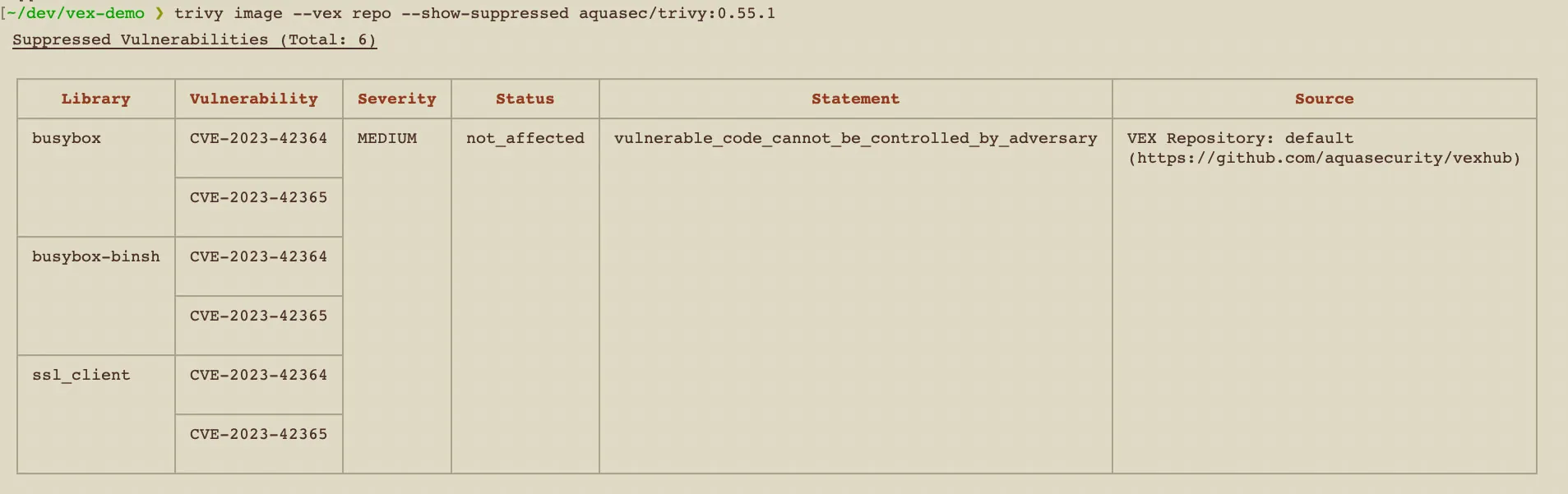
PRO TIPTo show suppressed vulnerabilities, add the optional |
In the near future Aqua customers will be able to take advantage of VEX Hub as part of the Aqua Platform scanner.
FAQ’sQ: What are the available alternatives to VEX Hub?As far as we know VEX Hub is the first and only open central repository of VEX statements. There are existing VEX implementations in scanning tools which deal with individual VEX files, or discovery of VEX document at scan time, but nothing like VEX Hub. Q: Who is validating the VEX statements that goes into VEX Hub?The VEX Hub model promotes the idea that VEX documents get committed into the package’s source code repository (instead of residing in VEX Hub itself). We trust the package maintainers as the authority for the software they produce. Each software project has its own process and criteria for committing code that you already trust (by using that code). And this trusted process applies to the VEX documents that they published too. For more detailed information, see here. Q: I’m a software maintainer, how do I report a false positive in a package I maintain?In a nutshell:
That’s it! For more detailed information, see here: Q: I’m a security vendor, how do I benefit from VEX Hub?You can consume VEX Hub just like Trivy does. The spec, code, data, and reference implementation are all open source. Feel free to collaborate on either project using GitHub Discussions or Pull Requests. Q: I’m an Operating System Distributor, how does VEX Hub impact me?As an OS Distro maintainer, you probably already manage a security advisory program with official vulnerability feeds. These feeds can and should include VEX information directly (without the need for VEX Repository). If you think that a separate VEX Repository makes sense in your case, you can stand up a VEX Repository by following the VEX Repository Specification. If you follow the specification, users will be able to use your VEX Repository seamlessly. Q: How is VEX different from ignoring vulnerabilities?Ignoring (e.g using .trivyignore file) or acknowledging vulnerabilities is meant for when users need to take a local decision to suppress vulnerability detections based on subjective criteria. VEX is meant to allow spreading broader general suppression that is widely applicable. For more about this topic, see here. |