CIS (Center for Internet Security) compliance scanning is a standard in Kubernetes (K8s) security and is widely adopted across the industry with implementations in several security scanners. Kube-bench, an open source project developed by Aqua Security was one of the first projects to provide Kubernetes CIS compliance scanning and became a staple in K8s security. As such it has been promoted by several larger organizations such as Amazon (EKS).
To expand upon its functionality while giving it the benefits of our other open source projects, CIS scanning was implemented into Trivy, Aqua Security’s all-in-one cloud native security scanner.
In this blog post, we detail the differences between the CIS scans performed by Kube-bench and the CIS scans done by Trivy, the benefits for our open source community, and how to get started with Trivy K8s compliance scanning.
CIS compliance scanning
CIS is a non-profit that provides recommendations on security best-practices. As part of their work, they have released a set of recommendations for configuring K8s clusters and workloads. The CIS benchmarks take a closer look not only at the running workloads but also at the infrastructure setup such as the Kubernetes components installed. Additional details on CIS benchmarks can be found in the Aqua cloud native wiki.
Aqua had previously built Kube-bench, an industry-leading open source tool for CIS compliance scanning, and now, these capabilities are integrated into Trivy for more comprehensive scanning and rich reporting.
Benefits of using Trivy over Kube-bench for CIS benchmark scanning
Kube-bench is a very popular tool to perform CIS compliance scanning. It has 6 thousand stars on GitHub and is supported by companies across the cloud native ecosystem.
Kube-bench is installed and runs as a K8s Job inside the cluster. However, this installation option makes it very difficult to integrate kube-bench with other cloud native tools or to manage changes to the installation over time. Furthermore, the scan reports are shared through the kube-bench pod logs of the completed Kubernetes Job. This makes reports difficult to access and short-lived, which in turn makes it difficult for users to compare reports over time.
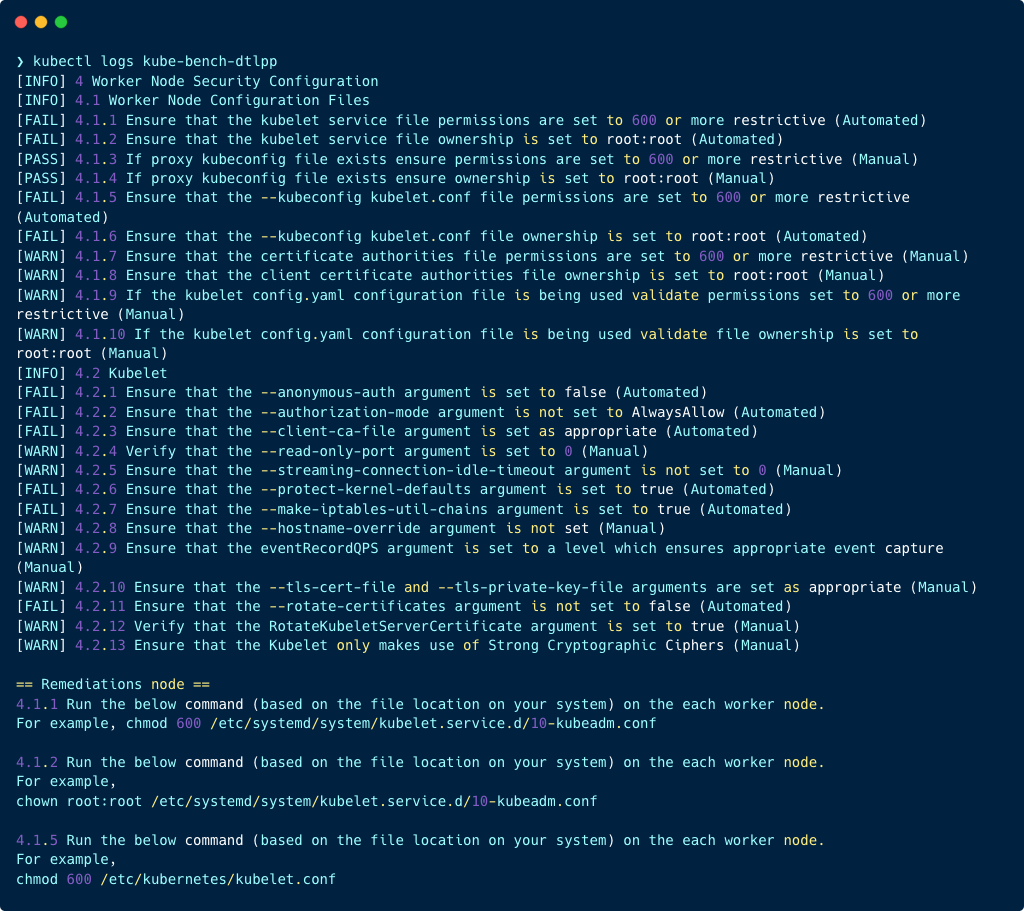
The screenshot below provides an example of the kube-bench CIS scan report from the logs:
Trivy started out as Vulnerability and Misconfiguration scanner but has since then expanded in functionality to become the most comprehensive, easy-to-use open source vulnerability and risk scanner, covering more languages, OS packages and application dependencies than any other open source scanner. .
Trivy can either be used as CLI tool on local machines, in CI pipelines or run as a Kubernetes Operator inside the cluster for continuous scans. This user experience is built upon the user input by a large open source community and industry best practices. Not only is it easy to run Trivy but also to integrate Trivy with existing cloud native tools. For instance, once Trivy is installed inside the Kubernetes cluster, it will automatically perform security scans. The reports can then be easily accessed in Grafana or similar open source tools.
To provide complete security scanning as part of Trivy, it became the logical next step to integrate compliance scanning, including CIS scans. Trivy is now able to perform CIS benchmark v1.23 scans, including scans on the Kubernetes nodes themselves. With kube-bench, users had to ssh into the nodes, install kube-bench and scan the node. Trivy on the other hand, automates everything as part of the same familiar Trivy CLI to generate full CIS reports easily from everywhere.
Additionally, Trivy also performs NSA benchmark checks and Pod Security Standard Scans to completely ensure cloud native environments are fully protected and compliant. Furthermore, by moving to Trivy teams can find benefit from Trivy’s workload scanning via the Kubernetes AP to discover further areas of concern provided with contextual practical results.
CIS guidelines consist of explicit checks, which are automatically tested and scored by the scanner, and abstract recommendations which are left for the user to manually check. Trivy Kubernetes scanning provided a more comprehensive report by automating those manual steps for you. A good example of this is –Section 5 – Policies in the CIS for Kubernetes benchmark which included many manual checks. These were skipped by other scanners but are now automatically tested by Trivy as part of CIS report generation.
Trivy Kubernetes scanning is based on a flexible generic compliance framework which allows anyone to easily implement more frameworks in a simple YAML configuration.
We highly recommend kube-bench users to migrate to Trivy to
- Make use of a large and growing developer community
- Access Trivy integrations with other cloud native tools
- Experience a superior user experience
- Access richer results thanks to Trivy’s multiple scanners, including vulnerability, workload misconfiguration, secret scanning and more.
Getting started with Trivy CIS Scanning
With the CLI
Prerequisites
- The Trivy CLI installed in your environment
CIS scans are part of the Trivy Kubernetes cluster scans and passed through the —compliance flag. Reports can either be requested as a summary table or as a detailed list:
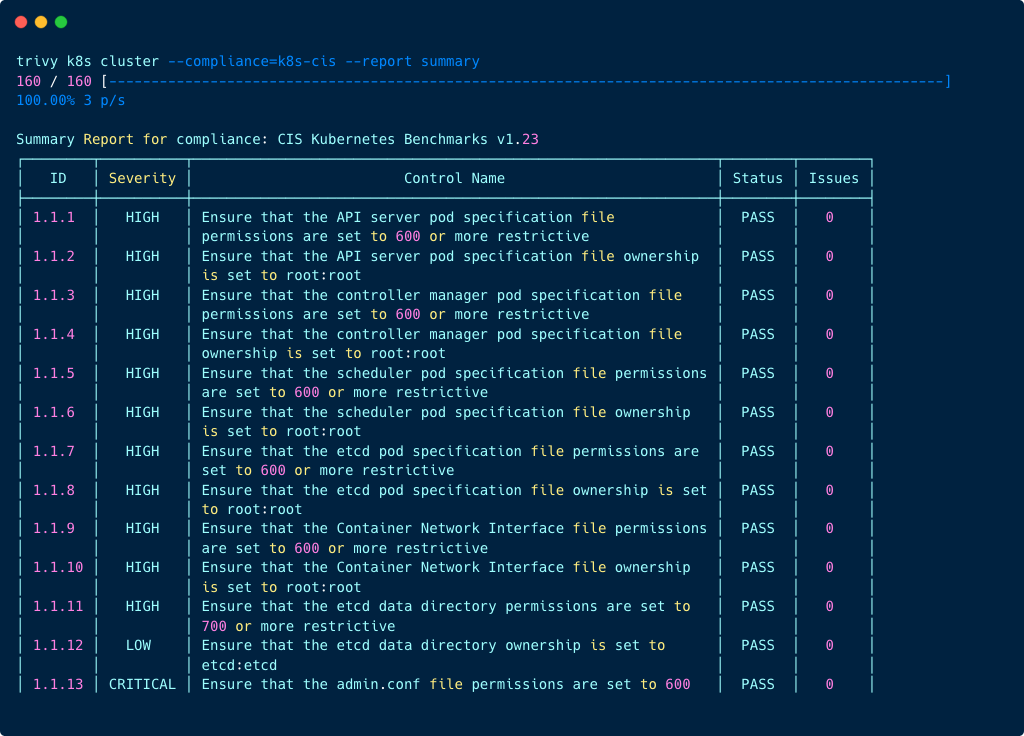
Summary Table
trivy k8s cluster --compliance=k8s-cis --report summary
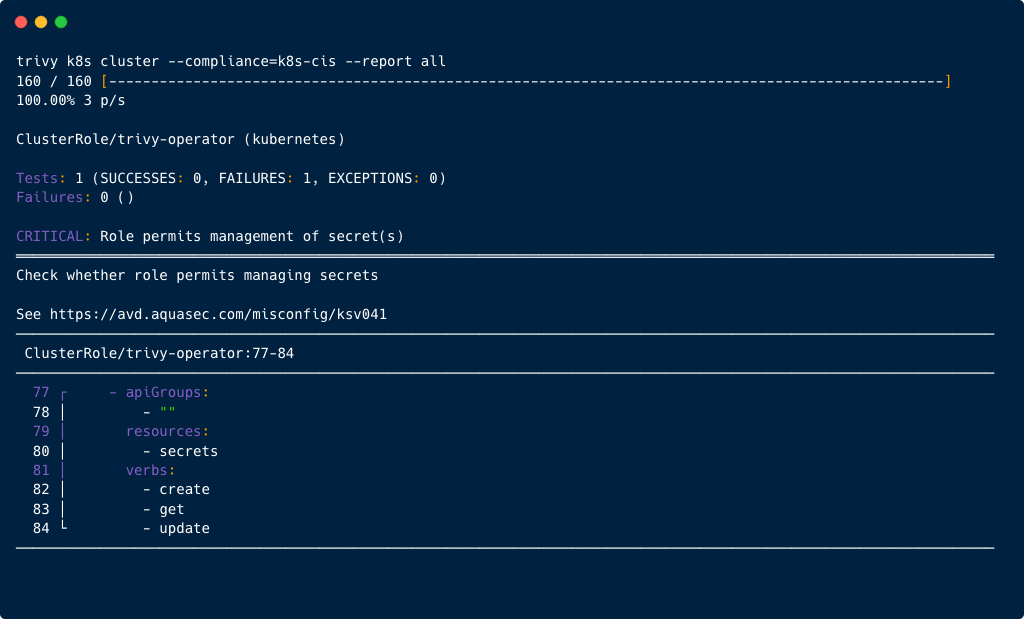
With details
trivy k8s cluster --compliance=k8s-cis --report all
With the Trivy Operator
Prerequisites
- Helm installed in your local environment
- Helm repo add aqua https://aquasecurity.github.io/helm-charts/
helm install trivy-operator aqua/trivy-operator
--namespace trivy-system
--create-namespace
--set="trivy.ignoreUnfixed=true"
--version 0.13.0
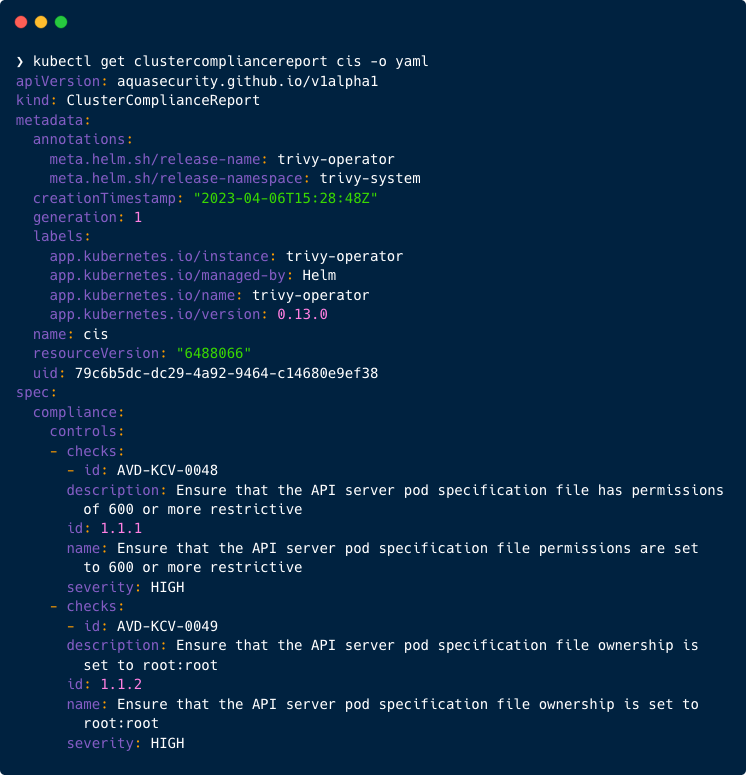
This will generate the full detailed compliance report inside the cluster. There are several ways that users can access the report. The Trivy Operator can be set to produce metrics based on the reports. These can then be visualised through Grafana. Alternatively, to access the CIS reports generated by the Trivy Operator directly through kubectl, the following kubectl command can be used:
kubectl get clustercompliancereport cis -o yaml
Alternatively, users can configure the operator to generate a more detailed report similar to the CLI instead.
The additional configuration can be found in the values.yaml file of the Helm Chart by setting -compliance.reportType to all.
helm install trivy-operator aqua/trivy-operator
--namespace trivy-system
--create-namespace
--set="trivy.ignoreUnfixed=true"
--set="compliance.reportType=all"
--version 0.13.0
We highly encourage you to try out Aqua Trivy CIS scanning. The documentation provides several additional examples to optimize your scan results.
If you enjoy using Aqua Trivy, we would highly appreciate if you could give us a Star on GitHub
Also, to stay up to date with the latest developments, join the Aqua Open Source Slack.

