In our view, making security tools easy to use is one of the best ways to increase adoption and help end users improve the security of their deployments. One of the strengths of our open source vulnerability scanner for container images, Trivy, is that it’s very easy to install and to integrate into different workflows. That’s not just our own opinion – Docker’s Security Lead, Justin Cormack, described Trivy as “incredibly easy to use and fast to scan”. But however easy we make Trivy to run as a standalone tool, it’s even easier to use when it’s pre-integrated into other parts of your system – for example, if your image registry automatically scans images for vulnerabilities.
To further reduce any barriers to integration, we’ve changed Trivy’s license from AGPL to the more permissive Apache 2.0 license. This Apache license has become the de facto standard license across cloud native open source software. It allows you use Trivy in any way you wish – all we ask is that you credit Aqua as the authors, as described in the license.
Trivy integrations with Harbor, Docker Enterprise, and more
We’re already seeing numerous integrations from some of the most popular image registries. For example, Trivy was one of the first scanners with a plug-in adapter for the Harbor registry. Following positive feedback from users, Trivy will be the default scanner from Harbor v2.0 onwards.
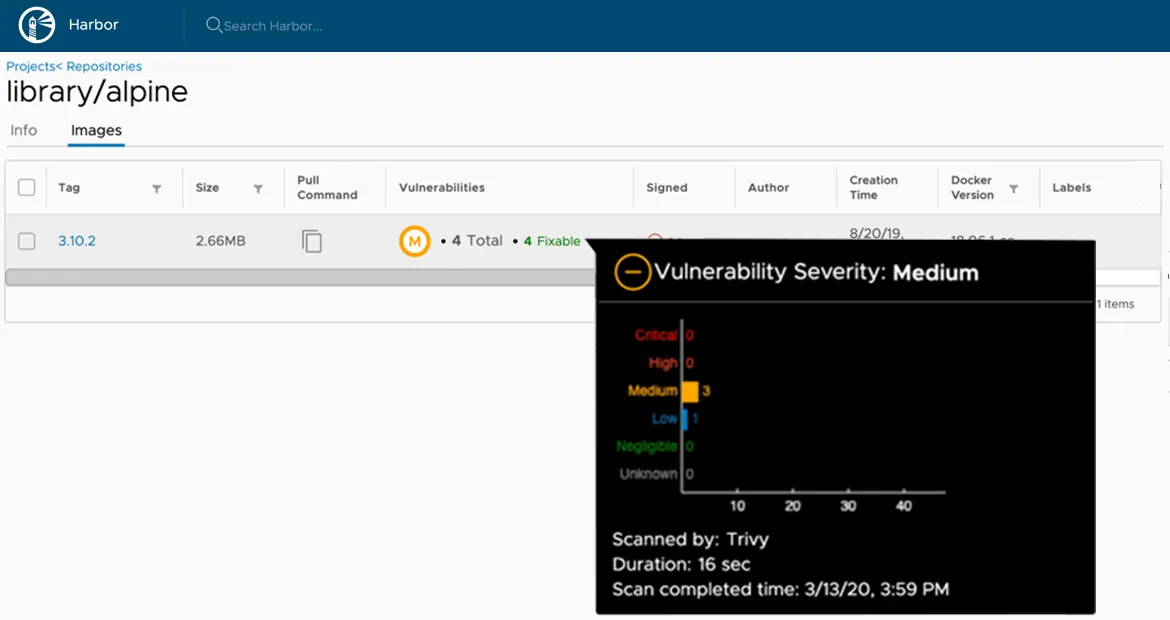
Figure 1 Trivy scan results within the Harbor registry
Similarly, we are working with the team at Mirantis on some Trivy enhancements to support them in building Trivy into their Docker Enterprise registry solution. Miland Gadre, VP of Engineering at Mirantis, says that “After evaluating several leading options for open source vulnerability scanning, Trivy really stood out.” We’ll be sure to keep you posted when that integration is available.
Integrations aren’t just limited to registries of course. Other folks in the community have also been hard at work creating integrations and add-ons for Trivy, such as this Prometheus exporter for extracting vulnerability metrics, and this Helm chart for installing Trivy into a Kubernetes cluster.
All these integrations are great news for end users, because they make it even easier to use Trivy within different environments. We know from experience that the more you use it, the more likely you are to find and eliminate important vulnerabilities from your deployed applications.
If you’ve got an idea for an integration or a new feature for Trivy, or would like to join our community in developing the world’s best open source vulnerability scanner, we’d love to hear from you on GitHub.

