Cloud Security Assessment: 8-Step Process and Checklist
Cloud security assessment is the process of evaluating the security posture of a cloud computing environment, such as a cloud service provider's infrastructure, platform, or software services. The goal is to identify and assess security risks and vulnerabilities in the cloud environment, as well as to evaluate the effectiveness of the security controls and measures that have been implemented to mitigate those risks.
What Is Cloud Security Assessment?
The assessment can cover various aspects of cloud security, including data privacy, data integrity, access control, identity and access management (IAM), network security, and compliance with relevant laws and regulations. It can be performed by internal security teams or by third-party security experts who are specialized in cloud security. The results of the assessment can help identify areas where improvements in cloud security are necessary and to create a plan to remediate any identified issues or vulnerabilities.
In this article:
Why Do You Need a Cloud Security Assessment?
A cloud security assessment is important for several reasons:
- Identify security risks and vulnerabilities: Cloud computing environments are complex and dynamic, and the risks and vulnerabilities can change rapidly. A cloud security assessment helps to identify these risks and vulnerabilities so that they can be mitigated.
- Ensure compliance: Many organizations are subject to regulatory compliance requirements, such as HIPAA, PCI DSS, and GDPR, that have specific requirements for cloud security. A cloud security assessment can help verify these requirements.
- Improve overall security posture: A cloud security assessment helps organizations to identify areas where improvements in cloud security are necessary. By addressing these issues, organizations can improve their overall security posture and reduce the risk of security breaches and data loss.
- Gain insight into the cloud environment: A cloud security assessment can provide valuable insight into the cloud environment, including the data and applications that are being used, the access controls in place, and the security risks associated with each component. This insight can be used to build a more comprehensive cloud security strategy.
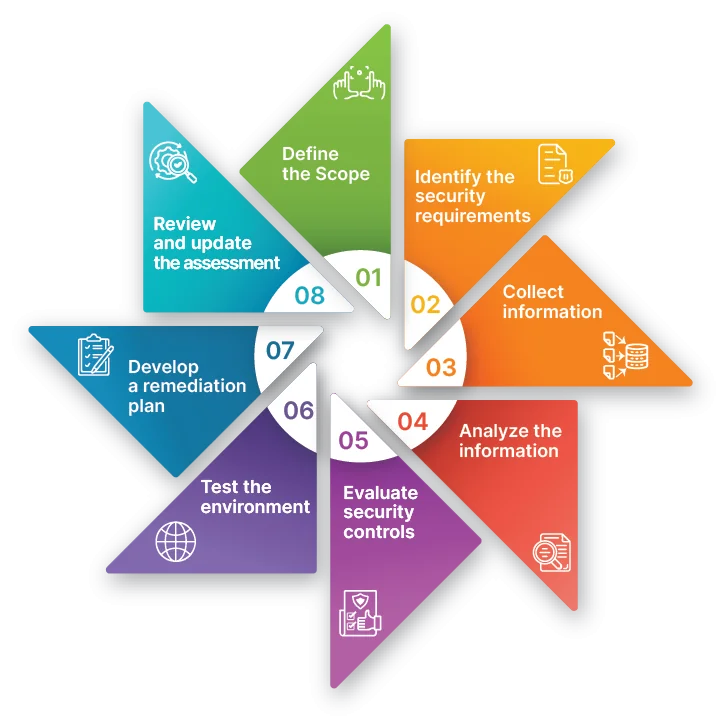
The Cloud Security Assessment Process
Cloud security assessments can be performed in various ways, but most assessments include some or all of the following steps:
- Define the scope: The scope of the assessment should be clearly defined to ensure that all relevant components of the cloud environment are evaluated.
- Identify the security requirements: Security requirements may come from various sources, such as regulatory compliance frameworks, industry standards, and internal policies. The security requirements help to ensure that the cloud environment is secure and compliant with relevant regulations.
- Collect information: Information about the cloud environment should be collected, including the configuration details of the components, network architecture, and access controls. This information is used to identify potential security risks and vulnerabilities in the cloud environment.
- Analyze the information: The information collected should be analyzed to identify potential security risks and vulnerabilities. This analysis may include identifying misconfigured components, unauthorized access, and other security issues.
- Evaluate security controls: The effectiveness of the security controls implemented in the cloud environment should be evaluated. This includes assessing access controls, encryption, network security, and other security measures to determine if they are sufficient to mitigate potential security risks and vulnerabilities.
- Test the environment: Vulnerability assessments and penetration testing should be conducted to identify additional security risks and vulnerabilities. These tests help to ensure that the cloud environment is resilient to attack and can withstand potential security threats.
- Develop a remediation plan: A remediation plan should be developed to address any identified security risks and vulnerabilities. The plan should prioritize the most critical issues and provide recommendations for mitigating them.
- Review and update the assessment: The cloud security assessment should be reviewed and updated regularly to ensure that it remains current and effective. This helps to ensure that the cloud environment is secure and can withstand potential security threats.
Cloud Security Assessment Checklist
Here are important aspects to include in a cloud security assessment:
Policies and Procedures
Policies and procedures are the foundation of any cloud security program. Reviewing the cloud provider’s policies and procedures is critical to ensure they align with the organization’s security requirements and compliance regulations. Identifying gaps in policies and procedures will help the organization understand where they need to focus their security efforts.
The policies should address the following:
- Access control and authentication
- Data protection and encryption
- Incident response and disaster recovery
- Auditing and logging
- Monitoring and reporting
- Compliance with relevant regulations and standards
Controlling Access
This assessment includes reviewing access controls and permissions to ensure they are appropriate for roles and responsibilities. Here are questions to help guide this assessment:
- Is access to the cloud environment restricted to authorized personnel only?
- Is two-factor authentication (2FA) enabled for all user accounts?
- Are strong passwords enforced?
- Are user accounts regularly reviewed and deactivated when necessary?
- Is there a process for granting temporary access and revoking access when it is no longer needed?
- Is access to sensitive data restricted based on job roles and responsibilities?
- Are third-party vendors granted access only when necessary and under a strict set of controls?
Network Security
Improper network access can lead to critical vulnerabilities. Here are aspects to verify when assessing network security in cloud environments:
- Are there firewalls in place to protect the cloud environment?
- Is traffic encrypted to protect data in transit?
- Are intrusion detection and prevention systems (IDPS) used to detect and prevent attacks?
- Are virtual private networks (VPNs) used to secure remote access?
- Is network segmentation used to isolate sensitive data and systems from the rest of the network?
Directory Services
Directory services are commonly used to manage user access and permissions. When assessing these services, ask the following questions:
- Are directory services used to manage user access and permissions?
- Are directory services regularly reviewed and updated?
- Are access controls in place to restrict access to sensitive data and systems?
Data Loss Prevention and Backup Policies
Data loss prevention (DLP) is important for preventing data from being lost, stolen, or misused. This part of the assessment should check:
- Which of the data is sensitive and needs to be protected? It is typically necessary to perform automated data classification to identify sensitive data.
- Is sensitive data encrypted at rest?
- Is there a backup policy in place to ensure that data can be restored in the event of a disaster?
- Are backups stored securely and offsite?
Security Operations
Here are aspects to consider when assessing security operations:
- Are security alerts monitored and investigated promptly?
- Are security incidents reported and escalated appropriately?
- Is there a process for conducting security incident response and remediation?
Encryption
Encryption is an important mechanism for protecting data in the cloud environment. Assess the following aspects of your cloud provider:
- Is data encrypted at rest using industry-standard encryption algorithms?
- Is data encrypted in transit to prevent interception and tampering?
- Is there a process for managing encryption keys?
Monitoring
Monitoring security events and logs is a critical component of cloud infrastructure. A cloud security assessment should review the following aspects:
- Are security events and logs monitored to detect and investigate potential security incidents?
- Are compliance audits performed regularly to ensure that the cloud environment meets industry and regulatory standards?
- Is there a process for reviewing and updating security controls based on changes in the threat landscape?
Related content: Read our guide to cloud security solutions
